What destroyed Hillary Clinton's campaign?
The obvious answer would be Barack Obama. But the destruction was accomplished through the agency of an Internet storm.
Those who remember the rapidity with which a story produced by 60 Minutes under the baton of Dan Rather was destroyed will know just how powerful an Internet storm can be.
In that instance, four documents were presented by 60 Minutes on September 8, 2004 -- less than 2 months before the scheduled Presidential election -- alleging that President Bush, who was standing for re-election had "disobeyed orders while in the Guard, and had undue influence exerted on his behalf to improve his record". It was an accusation that was potentially devastating to Bush. On September 8 a reasonable observer would have made the linear projection that Bush's re-election was doomed. But complex systems work in non-linear ways.
A confluence of factors explosively combined to generate a memetic storm. Small Internet sites, each insignificant by itself, began to resonate with the word that the 60 Minutes documents were faked. A variety of technical experts, drawn by what was effectively an open-source debugging exercise, found fault after fault with the documents. Within four days not only was the 60 Minutes expose discredited but reversed upon itself. By September 10, CBS News was internally admitting doubts about the 60 Minutes story. By September 11, 2004, the network was beginning to backpedal. Eventually the documents would be shown to be fakes. The scandal would cause the removal of high CBS officials, rip up the 60 Minutes news team which prepared the show and effectively ended the career of anchor Dan Rather.
It was the first public demonstration of an Internet storm.
Source: The Belmont Club
Commentary
The following won't make sense until you have read the entire post at Wretchard's:
Swarm Intelligence! Also, I wonder if there is a possibility a very adept organization could leverage this type of event if they identified the key (b)logs.
Blogging the world around me.
Notice
I am working on the template of this blog today in order to chase down some problems that have developed with my template and widgets.
Contact & Crowd Funding

To submit releases for publication, email me here. This includes Guest Commentaries. If you have a photo that you wish me to use with your press release or article, please send it to me, otherwise I'll use whatever I feel best fits your article.
Letters to the Editor
Send Letters to the Editor to editor@MaconMedia. Limit is one submission every seven days. You may include photos, video or audio. Submissions will be edited for vulgarity or similar reasons. Limit submissions to less than 10,000 words. LOL
For a quicker response, send me a message on Twitter or add me to a circle on Google Plus and send it just to me.
If you have been sending me press releases via my private email address, that will continue to work just fine. The Twitter or Google+ account will get my attention quicker.
For a quicker response, send me a message on Twitter or add me to a circle on Google Plus and send it just to me.
If you have been sending me press releases via my private email address, that will continue to work just fine. The Twitter or Google+ account will get my attention quicker.
NON PROFIT OR CIVIC EVENTS
Macon Media will promote nonprofit or civic events if contacted by an organizer of the event. This includes rallies, protests, community forums, and parades. Messeanger Link http://m.me/MaconMediaNews


CROWD FUNDING
If you're of a mind, and can afford it, a dollar a month (or more) from enough people will make a huge difference in improving the quality of coverage of local meetings and events, as well as allowing remote weather stations and weather cams to be deployed throughout the county that you will be able to access online.
Currently, 20 people have pledged $99 a month. This is a tremendous help. Please visit www.patreon.com/MaconMedia for more information on how to contribute.
Businesses can underwrite this coverage by day sponsorships, surplus equipment donations, etc. Inquire at editor@maconmedia.com for more information.


Popular Posts
-
PRESS RELEASE NCDOT date: November 12, 2016 contact: David Uchiyama Fire Closes Popular Western Highway Nantahala Gorge Closed ...
-
Here is another press release from the US Forest Service on the various fires in our region. The information does not include fires that...
-
Des Moines Register.....CNN/Opinion Research * Mike Huckabee 32% (29%)...........28 * Mitt Rom...
-
According to this press release from Colonial Pipeline, construction of a bypass line has been completed and testing will be taking place...
-
Macon County is under a State of Emergency effective at 8 pm tonight, according to a document signed at 11 am yesterday and just sent to M...
Copyright Notice
Copyright © 2005-2018 Bobby Coggins
Google
My Facebook Pages
Other WNC Citizen Journalists
Blogs
WNC SCAN
Other Local Media Sources
Macon County News and Shopping Guide
WFSC-AM
Highlands Newspaper
The Franklin Press (beware of paywall)
Weather Center
West of the Balsams
Badges and Buttons
Tweet to @ThunderPig Personal Account
Tweet to @WPIG Public Policy Account
Tweet to @WNCscan Radio Monitoring Account
Blogroll
I've removed the RPC Widget. I'll be replacing it with a regular blogroll soon.
Facebook Widget
-Live Breaking News-
Feedjit
The Counterjihad
1389 Blog
4-Block World
The 910 Group Blog
The Acton Institute
All About Muhammad
All Things Beautiful
Always on Watch
American Enterpirse Institute
An American Expat in Southeast Asia
The American Thinker
The Anchoress
Anti-Idiotarian Rottweiler
Are We Lumberjacks?
The Astute Blogger
Atlas Shrugs
Average Gay Joe
Babalu Blog
Balder Blog
Ballot, Soap, Jury, Ammo
Barcepundit
Bare Naked Islam
Beer n Sandwiches
Belmont Club
Robert Bidinotto
The Big Feed
Big Lizards
Bill's Comments
Birdbrain
Black and Right
The Black Sphere
Blog of the Gods (Mexican Drug War)
Bloomberg News
Blowing San #1
Stephen Bodio’s Querencia
Andrew Bolt
Andrew Bostom
Brain Surgery With Spoons (mp3s)
Breath of the Beast
Breitbart News
Brits At Their Best
Brothers Judd
Tammy Bruce
Bruges Group Blog
Brushfires of Freedom
The Brussels Journal
Brutally Honest
Bullets and Beer
The Business of America is Business
Byzantine Sacred Art Blog
CAIR Watch
The Canadian Sentinel
Carib Pundit
carnage and culture
Cavatus’s Blog
CDR Salamander
Phyllis Chesler
Chitral News
Christian Action Network
City Journal
Classical Values
Coalition of the Swilling
The Common Room
Conservative Swede
The Conspiracy to Keep You Poor and Stupid
Constantinople Again
The Counter-Jihad Initiative
Counterterrorism Blog
Cox & Forkum
Cranmer
Creeping Sharia
Cripes Suzette
Crusader
Cuanas
Daily Pundit
Danish Affairs
Defense News
Democracy Project
Deus Vult
The Devil's Kitchen
Dinocrat
The Dissident Frogman
The Dividend Guy
DowneastBlog
Ed Driscoll
Dry Bones (cartoons)
Kim du Toit
Dumb Still Looks Free
Dutch Defence League
Dyspepsia Generation
EagleSpeak
e-Claire
EDL Extra
Eject! Eject! Eject!
Elder of Stockholm
Eleanor Duckwall's Spotlight
Eleven North
Erica’s Blog
Eteraz.org: States of Islam
Eternity Road
EU Referendum
Eurabia (Netherlands)
Eurabian Farm
Eurabian News
Europe News
European Shooter
eViscera
Eye of Polyphemus
Falkblick
Fausta’s Blog
The Fight Against Jihad
Eamonn Fitzgerald’s Rainy Day
Five Feet of Fury
fjordman
Flopping Aces
Florida Cracker
Floyd VA: Making Ripples
Foehammer's Anvil
Forum mot islamisering (Sweden)
Foundation for the Defense of Democracies
The Fourth Rail
Français de Souche
Fred on Everything
Fresh Bilge
Fresh Tasty Ideas
FrontPage
Fundamentally Right
GalliaWatch
Gates of Lisbon
Gateway Pundit
Gates of Vienna
Gay and Right
GDCritter
gegen-islamisierung
Gegenstimme
GeoPoliticalReview
Norm Geras
The Gertz File
Ghost of a flea
Global Politician
Green’s Piece
Grouchy Old Cripple
Gypsy Scholar
Hank's Eclectic Meanderings
Daniel Hannan
Victor Davis Hanson
Herouxville Town Charter
Het Vrije Volk
Hugh Hewitt
Hibernia Girl
Hillbilly Politics
Hodjas Blog
Mikkel Høgh
Hommaforum
Hot Air
Human Rights Service
Mark Humphrys (Irish Libertarian)
Hyscience
In From the Cold
The Indian National Interest
Indus Valley Rising
Infidel Bloggers Alliance
Instapundit
Intergalactic Source of Truth
International Civil Liberties Alliance
International Free Press Society
Iowahawk
Iraq the Model
The Islamic Threat
Israel Matzav
Jeremayakovka
Jihad Watch
Jillosophy
Johnny Dissidemce
Joshua Pundit
July 4th Tea Party Patriots
Kerfuffles
Kesher Talk
Khalas!
Kingdom of Chaos
Klein Verzet
Kudlow's Money Politics
Larwyn’s Linx
Let Them Fight or Bring Them Home!
Mark Levin
Libertarian Leanings
Liberty and Culture
Life in INGSOC
Lileks -- Bleat
LionHeart
Lisistrata
Livingscoop
Lock and Load
L’Ombre de l’Olivier
Long-lasting Islamophobia
Macsmind
Maggie’s Farm
Michelle Malkin
Manfreds politische Korrektheiten
Mausers, Medicine, & Motorcycles
Maverick Philosopher
Maxed Out Mama
Mesopotamia West
Brian Micklethwait
Middle East Info
Mightiest of the Nine
Mission Europa Netzwerk Karl Martell
Mitt Sverige
Moonbattery
Mr. O’Brian’s Thinking Emporium
Mythusmage Opines
Neddy’s Palaver
The Neighborhood of God
Neuromante
A New Dark Age Is Dawning
The New English Review
News from Norway
No Oil For Pacifists
¡No Pasaran!
Noblesse Oblige
Northern Virginiastan
Notoriously Conservative
Nourishing Obscurity
NRO
Obi's Sister
Occidental Soapbox
Ocean Guy
On the Wing
One Cosmos
One STDV
Online Defense and Acquisition Journal
Open Europe Blog
The Opinionator
Oraculations
The Other McCain
Oz Conservative
Patriot's Corner
patruped:bun biped:rau
Peace Like A River
Pedestrian Infidel
The People's Cube
Philippines Phil
Pigs de Resistance
The Pink Flamingo Bar and Grill
Daniel Pipes
Planck's Constant
Point Five
Polder & Levant
Polemiken
Police Inspector Blog
PoliGazette
Political Beach Girl
Political Pistachio
Politically Incorrect
The Politics of CP
Posse Incitatus
Power and Control
Power Line
Principled Discovery
Protein Wisdom
Provocateur
Pundita
Queer Conservative
Quid Nimis
The Radio Patriot
Raman's Terrorism Analysis
Random Traverse
Rantburg
Rants and Raves
Rebellious Vanilla
Red Alerts
Redneck’s Revenge
Refugee Resettlement Watch
Regime Change Iran
The Religious Policeman
The Return of Scipio
Amy Ridenour’s National Center Blog
Riehl World View
Right Side News
Rightwing Nuthouse
rightwingdeathbogan
Roncesvalles
G.M. Roper
Doug Ross
Rubin Reports
The Russell Kirk Center
Sad Old Goth
Say Anything
Isaac Schrödinger
The Scratching Post
Seraphic Secret
Seriously Sandeep
The Shield of Achilles
Silent Running
Small Dead Animals
Small Precautions
Snaphanen
Snouck Hurgronje
SOS – Österreich
State of Flux
Mark Steyn
Stop the ACLU
Stop the Islamisantion of Europe
Stop the Islamization of Denmark
Stop the Madrassa
Strategy Page
Suicide of the West
summer patriot, winter soldier
Sunlit Uplands
Swenglish Rantings
Taylor & Company
Technicalities
The Technology Liberation Front
The Ten O’Clock Scholar
Tenth Amendment Center
ThreatsWatch
Thunder Pig
The Thunder Run
TigerHawk
Tizona’s Weblog
To the Point News
Torchlight
Michael Totten
Truth & Consequences
Tundra Tabloids
Turban Bomb
Una via per Oriana
The Unoriginal Muse
Up Pompeii
Urban Grounds
Uriasposten
Vasarahammer
View from the Right
Viking Observer
Villainous Company
Vlad Tepes
David Warren
Washington Rebel
The Washington Times
Watcher of Weasels
Webloggin
Diana West
The West’s darkest hour
Western Civilization and Culture
Western Resistance
Sissy Willis
Winds of Change
Winds of Jihad
Wintery Knight
Wizbang
World History Blog
Yet Another Really Great Blog
La Yijad en Eurabia
Michael Yon
Yorkshire Miner
Zonka på Dansk
Zoon Politikon
Powered by Blogger.
Followers
Labels
- \ ( 1 )
- 08 ( 1 )
- 110th Congress ( 65 )
- 111th Congress ( 40 )
- 112th Congress ( 17 )
- 113th Congress ( 5 )
- 117th Congress ( 2 )
- 118th Congress ( 4 )
- 1964 Flood ( 1 )
- 1985 Cold Wave ( 1 )
- 1A5 ( 1 )
- 2006 ( 2 )
- 2007 ( 1 )
- 2008 ( 393 )
- 2009 ( 6 )
- 2010 ( 90 )
- 2011 ( 19 )
- 2012 ( 104 )
- 2012 Election ( 42 )
- 2012. Republican Party ( 1 )
- 2013 ( 4 )
- 2014 ( 1 )
- 2014 Cold Wave ( 1 )
- 2016 ( 1 )
- 2016 Education ( 6 )
- 2016 Election ( 2 )
- 2016 Franklin Town Board Meetings ( 2 )
- 2016 Macon Commissioner Meetings ( 2 )
- 2016 Severe Weather Week ( 1 )
- 2016 State Legislature ( 3 )
- 2016 Wildfires ( 3 )
- 2017 ( 2 )
- 2017 Aldermen ( 15 )
- 2017 Education ( 5 )
- 2017 Education Budget ( 2 )
- 2017 Elections ( 4 )
- 2017 HUrricane Season ( 15 )
- 2017 Macon Budget ( 4 )
- 2017 Macon Commissioner Meetings ( 10 )
- 2017 Meetings ( 2 )
- 2017 State Legislature ( 3 )
- 2017 Town Council ( 10 )
- 2017 Town Retreat ( 1 )
- 2018 Almanac ( 45 )
- 2018 Budget Work Session ( 3 )
- 2018 Deaths ( 1 )
- 2018 Early Voting Numbers ( 2 )
- 2018 Education ( 4 )
- 2018 Education Budget ( 2 )
- 2018 Elections ( 24 )
- 2018 Franklin Planning Board Meetings ( 2 )
- 2018 Franklin Town Council Meetings ( 16 )
- 2018 Hurricane Season ( 1 )
- 2018 Macon County Commissioner Meetings ( 20 )
- 2018 Primary ( 8 )
- 2018 Special Events ( 1 )
- 2018-2019 Budget ( 2 )
- 2018-2019 School Year ( 3 )
- 2019 CIviv Events ( 1 )
- 2019 Elections ( 7 )
- 2019 Franklin Town Council ( 15 )
- 2019 HUrricane Season ( 11 )
- 2019 Macon County Board of Commissioner Meetings ( 14 )
- 2019 Macon County Planning Board Meetings ( 2 )
- 2019 Meetings ( 2 )
- 2019 October ( 1 )
- 2019 State Legislature ( 5 )
- 2019-2020 county budget ( 6 )
- 2019-2020 town budget ( 4 )
- 2020 Board of Education ( 3 )
- 2020 County Budget ( 3 )
- 2020 COVID in the Schools ( 16 )
- 2020 elections ( 28 )
- 2020 Franklin Budget ( 2 )
- 2020 Franklin Planning Board Meetings ( 1 )
- 2020 Franklin Town Council ( 17 )
- 2020 Macon County Board of COmmissioner Meetings ( 13 )
- 2020 Wildfires ( 1 )
- 2020-2021 Budget ( 5 )
- 2021 Board of Education ( 5 )
- 2021 Budget ( 2 )
- 2021 COVID in the Schools ( 27 )
- 2021 elections ( 3 )
- 2021 Franklin Town Council ( 13 )
- 2021 General Assembly ( 1 )
- 2021 Hurricane Season ( 1 )
- 2021 Macon County Board of Commissioners ( 11 )
- 2021 Severe Weather ( 2 )
- 2021-2022 Budget ( 4 )
- 2022 Cold Wave ( 3 )
- 2022 Deaths ( 2 )
- 2022 Education ( 3 )
- 2022 Elections ( 11 )
- 2022 Events ( 2 )
- 2022 Franklin Town Council ( 6 )
- 2022 Hurricne Season ( 1 )
- 2022 Macon County Board of Commissioners ( 8 )
- 2022 Macon County Board of Education ( 4 )
- 2022 National News ( 2 )
- 2022 Severe Weather ( 2 )
- 2022 Town Retreat ( 1 )
- 2022 w ( 1 )
- 2022 Weather ( 294 )
- 2022-2023 Budget ( 4 )
- 2023 0519 ( 1 )
- 2023 Deaths ( 2 )
- 2023 Education ( 5 )
- 2023 Election ( 1 )
- 2023 Franklin Town Council Meetings ( 4 )
- 2023 Macon COunty Board of Commissioners ( 8 )
- 2023 National News ( 1 )
- 2023 Severe Weather ( 5 )
- 2023 Weather ( 352 )
- 2023 Wildfires ( 12 )
- 2023 Winter ( 3 )
- 2023-2024 Budget ( 3 )
- 2024 Cold Wave ( 2 )
- 2024 Education ( 3 )
- 2024 Election ( 9 )
- 2024 Franklin Town Council ( 6 )
- 2024 Hurricane Season ( 1 )
- 2024 Local Government Meetings ( 2 )
- 2024 Macon County Board of COmmissioners Meetings ( 12 )
- 2024 Macon County Board of Education Meetings ( 6 )
- 2024 Weather ( 354 )
- 2024 Wildfires ( 1 )
- 2024 WInter ( 1 )
- 2024-2025 Budget ( 4 )
- 2025 Election ( 1 )
- 2025 Franklin Town Council ( 1 )
- 2025 Macon County Board of Commissioners ( 6 )
- 2025 Weather ( 336 )
- 2025 Wildfires ( 20 )
- 2025 Winter ( 8 )
- 2025-2026 Budget ( 4 )
- 2026 Elections ( 1 )
- 2026 Macon County Board of Commissioners ( 2 )
- 2026 Weather ( 18 )
- 208 ( 1 )
- 287 (g) ( 1 )
- 4-H ( 1 )
- 43rd Prosecutorial District ( 5 )
- 4th Fleet ( 2 )
- 5GW ( 23 )
- 9-12 Project ( 5 )
- 9/11 Replay ( 13 )
- 910 ( 36 )
- 911 Retards ( 10 )
- 911 Road Names ( 1 )
- A Cautionary Tale ( 7 )
- ABC Board ( 2 )
- Abortion ( 18 )
- AC-T ( 18 )
- accident ( 5 )
- Accuracy in Media ( 1 )
- aclu ( 1 )
- Action Alert ( 46 )
- Action Club ( 4 )
- Activism ( 72 )
- ad ( 1 )
- Adam Conley ( 1 )
- adam kokesh ( 1 )
- Adam Savage ( 1 )
- adventure ( 4 )
- Advisories Watches and Warnings ( 164 )
- Aerial Footage ( 1 )
- Aetna ( 1 )
- Affordable Care Act ( 1 )
- Afghanistan ( 13 )
- AFP ( 4 )
- Africa ( 18 )
- AI ( 1 )
- AIM ( 1 )
- Air Quality ( 8 )
- aircraft ( 3 )
- Aircraft Crash ( 8 )
- Airport ( 6 )
- al fin ( 14 )
- al gore ( 9 )
- Al Pisano ( 1 )
- Al Slagle ( 4 )
- al-Qaeda ( 10 )
- Alan Keyes ( 1 )
- ALBERTO ( 11 )
- Alcohol ( 6 )
- alert ( 30 )
- Alexander Hailton ( 1 )
- Alexander Hamilton ( 1 )
- ALIPAC ( 8 )
- Allison Outdoor Advertising ( 1 )
- Almanac ( 15 )
- Altered Frequencies ( 1 )
- Alternative Energy ( 9 )
- Amanda Gorman ( 1 )
- Amateur Radio ( 1 )
- Amber Alert ( 7 )
- ambient ( 1 )
- america ( 201 )
- American History ( 1 )
- American Recovery Plan ( 1 )
- American Revolution ( 3 )
- Americans for Prosperity ( 1 )
- Amnesty ( 2 )
- Amy Coney Barrett ( 1 )
- Anarchists ( 12 )
- andrew meyer ( 1 )
- Android ( 1 )
- Angel Medical Center ( 58 )
- Animal Control ( 5 )
- Ann Romney ( 1 )
- Announcements ( 44 )
- Annual Audit ( 1 )
- Annual Traditions ( 1 )
- Anonymous ( 1 )
- Anonymous Tips ( 1 )
- anti-American protesters ( 59 )
- anti-Semitism ( 20 )
- Anton Bruckner ( 1 )
- Any Way You Like It ( 5 )
- Appalachia ( 45 )
- Appalachian Animal Rescue Center ( 1 )
- Appalachian Trail ( 6 )
- Apple ( 2 )
- Applications ( 1 )
- appointments ( 1 )
- april ( 2 )
- April 2019 Franklin Town Council ( 1 )
- April 2019 Local Government Meetings ( 3 )
- April 2019 Weather ( 32 )
- April 2020 COVID-19 Update ( 35 )
- April 2020 Local Government ( 3 )
- April 2020 Weather ( 30 )
- April 2021 COVID-19 ( 6 )
- April 2021 Local News ( 1 )
- April 2021 National News ( 3 )
- April 2021 Public Safety ( 1 )
- April 2021 Weather ( 29 )
- Arbor Day ( 1 )
- Archive ( 1 )
- Archives ( 3 )
- Argentina ( 1 )
- Arizona ( 1 )
- armed revolution ( 19 )
- Arms ( 1 )
- ARPA ( 1 )
- Art Pope ( 1 )
- Art Provencher ( 1 )
- Artemis 1 ( 4 )
- Artemis Program ( 2 )
- ARTHUR ( 1 )
- ARTHUR 2020 ( 1 )
- Arts ( 1 )
- asheville ( 159 )
- Asia ( 9 )
- assassination ( 2 )
- astronomy ( 63 )
- asville police ( 2 )
- Audio ( 23 )
- August 2018 Curt Docket ( 1 )
- August 2018 Public Safety ( 1 )
- August 2018 Weather ( 51 )
- August 2019 Local Government Meetings ( 2 )
- August 2019 Weather ( 30 )
- August 2020 COVID-19 ( 27 )
- August 2020 Local Government Meetings ( 3 )
- August 2020 Weather ( 24 )
- August 2021 COVID-19 ( 22 )
- August 2021 Local Government Meetings ( 3 )
- August 2021 Weather ( 33 )
- Automated Post ( 102 )
- Automobiles ( 1 )
- Autumn ( 20 )
- Avian Flu ( 4 )
- B5 ( 1 )
- Babylon 5 ( 5 )
- Barack Obama ( 394 )
- Barack Soetoro ( 1 )
- Barbara Bush ( 1 )
- Barbara McRae ( 5 )
- BARRY 2019 ( 6 )
- BCGOP ( 10 )
- bear ( 1 )
- Bees ( 5 )
- Bell Tolling ( 1 )
- Benefit ( 3 )
- Benefit Dinner ( 2 )
- Benjamin Netanyahu ( 2 )
- BepiColombo ( 1 )
- Bernie sanders ( 1 )
- BERYL ( 4 )
- BETA 2020 ( 1 )
- Betsey Gooder ( 1 )
- Betty Cloer Wallace ( 3 )
- Beverly Perdue ( 18 )
- BIA ( 2 )
- bill Clinton ( 13 )
- Bill Graham ( 4 )
- Bill Harrell ( 1 )
- Bill O'Relliy ( 2 )
- Bill Whittle ( 1 )
- Billy Graham ( 2 )
- Billy Mashburn ( 4 )
- bird ( 1 )
- birds ( 11 )
- BizWeek ( 1 )
- Black Liberation Theology ( 2 )
- Black Lives Matter ( 3 )
- Black Mountain ( 1 )
- black swan ( 1 )
- Blackwater ( 1 )
- bleg ( 1 )
- Blizzard of 1993 ( 2 )
- blog burst ( 53 )
- Blog Talk Radio ( 90 )
- blogburst ( 24 )
- blogger spam ( 2 )
- Blogger Tips ( 10 )
- Blogs ( 86 )
- blooms ( 1 )
- Blue Dog ( 9 )
- Blue NC ( 4 )
- Blue Origin ( 3 )
- Blue Ridge Bartram Trail Conservancy ( 1 )
- Blue Ridge Parkway ( 4 )
- Blue Zones ( 1 )
- Board of Elections ( 3 )
- Bob carpenter ( 2 )
- Bob Dole ( 1 )
- Bob Etheridge ( 3 )
- Bob Orr ( 3 )
- Bob Scott ( 10 )
- Bob Simpson ( 3 )
- Bobby Coggins ( 1 )
- Bobby Jindal ( 2 )
- Bobby Kuppers ( 7 )
- Bombing ( 1 )
- book ( 4 )
- Books ( 9 )
- Boston Marathon Bombing ( 1 )
- Bramlett Ridge ( 1 )
- Brandon McMahan ( 1 )
- brandon randolph ( 1 )
- Brasstown Ringers ( 4 )
- breaking news ( 165 )
- Breck Girl ( 1 )
- Brian McClellan ( 3 )
- Brian Sitnick ( 1 )
- Bridal Veil Falls ( 2 )
- Bringing It To Life Productions ( 1 )
- British MOnarchy ( 2 )
- broadband ( 4 )
- Bryan Carpenter ( 2 )
- Bryan Rauers ( 1 )
- Bryson City ( 2 )
- BSG ( 16 )
- budget ( 105 )
- buildings ( 1 )
- Buncombe Commissioners ( 2 )
- Buncombe County ( 91 )
- bureaucrats ( 3 )
- burn ban ( 13 )
- Burninftown-Iotla VFD ( 1 )
- Burningtown VFD ( 5 )
- Bus Fire ( 1 )
- Bust Your Butt Falls ( 1 )
- C-17 ( 1 )
- CAGW ( 17 )
- CAIR ( 1 )
- Calendar ( 6 )
- California ( 1 )
- Callista Bisek ( 1 )
- Camp Branch Fire ( 4 )
- Campaign ( 142 )
- Campain for Liberty ( 1 )
- Canada ( 1 )
- cancer ( 1 )
- Candidate Forum ( 12 )
- candidates ( 76 )
- Candlelight Service ( 2 )
- Candlelight Vigil ( 1 )
- Cap ( 2 )
- Capitalism ( 4 )
- carbon credits ( 1 )
- Care Partners ( 1 )
- CareNet ( 2 )
- Caribbean ( 1 )
- Carl Mumpower ( 92 )
- Carol Arnold ( 1 )
- Carolina Conservatives ( 1 )
- Carolina Stompers ( 41 )
- CBS ( 1 )
- CChurch of Jesus Christ of Latter-day Saints ( 1 )
- Cecil Bothwell ( 8 )
- censorship ( 25 )
- Central Committee ( 1 )
- Certificate of Need ( 1 )
- CFL ( 1 )
- Chad Nesbitt ( 6 )
- changes ( 1 )
- Charity Event ( 2 )
- Charles Andrew Cochran ( 1 )
- Charles Taylor ( 7 )
- Charles Thomas ( 3 )
- Charlie Greenwood ( 1 )
- Charlie Leatherman ( 1 )
- Che Guevara ( 3 )
- Chemistry ( 1 )
- Cheoh NF ( 2 )
- Cherokee ( 10 )
- Cherokee County ( 5 )
- Cherokee One Feather ( 1 )
- Chet Edwards ( 1 )
- chief hogan ( 1 )
- ChildCare ( 1 )
- China ( 11 )
- Chinese Aggression Watch ( 6 )
- Chinese Spy Balloon ( 1 )
- Chips ( 2 )
- CHRIS ( 4 )
- Chris Christie ( 1 )
- Chris Petrella ( 3 )
- Christian ( 81 )
- Christmas ( 75 )
- Christmas 2018 ( 6 )
- Christmas 2019 ( 3 )
- Christmas 2020 ( 3 )
- Christmas 2021 ( 2 )
- CHRISTMAS 2022 ( 8 )
- CHristmas 2023 ( 3 )
- Christmas 2024 ( 5 )
- Christmas 2025 ( 1 )
- CHuck Edwards ( 1 )
- Church News ( 1 )
- Cicero ( 1 )
- cirrus ( 3 )
- citizen jornalism ( 23 )
- citizen journalism ( 807 )
- Citizen Science ( 1 )
- Citizens For Change ( 1 )
- Citizens Speak ( 1 )
- City Council ( 16 )
- Civic Organizations ( 1 )
- civil disobedience ( 1 )
- civil obedience ( 1 )
- Civil War ( 26 )
- Civility ( 1 )
- Civitas ( 1 )
- Civitas Institute ( 2 )
- Clarks Chapel VFD ( 3 )
- Class Warfare ( 2 )
- CLAUDETTE 2021 ( 2 )
- Clay County ( 3 )
- Clean Coal ( 1 )
- Clerk of Court ( 1 )
- Clifton Ingram ( 1 )
- Climate ( 14 )
- Climate Pollution Reduction Grant ( 1 )
- Clint Kendall ( 1 )
- closed meeting ( 4 )
- clouds ( 51 )
- cnn ( 1 )
- CodeRED ( 1 )
- Cold and Flu ( 7 )
- Cold for a Cause ( 3 )
- Cold Snap ( 1 )
- Cold Wave ( 16 )
- Colin Powell ( 1 )
- Colonial Pipeline ( 5 )
- Columbus Day ( 5 )
- column ( 26 )
- comet ( 1 )
- Comet 46P/Wirtanen ( 1 )
- commenatry ( 5 )
- commentary ( 57 )
- comments ( 2 )
- commissioners ( 1 )
- Committees ( 61 )
- common sense ( 4 )
- Communications ( 1 )
- Communism ( 44 )
- Community Activites ( 3 )
- Community Funding Pool ( 2 )
- Community Garden ( 1 )
- Comprehensive Plan ( 5 )
- Concepts ( 304 )
- concert ( 5 )
- Congress ( 5 )
- congressman ( 2 )
- Connections ( 1 )
- Consent Agenda ( 1 )
- Conservatism ( 165 )
- conservative activism ( 61 )
- Conservative Counter Protest ( 41 )
- Conservative Revolution ( 20 )
- conservative talk ( 61 )
- Conservative Thunder ( 32 )
- conspiracy theories ( 13 )
- Constellation Program ( 1 )
- constitution ( 4 )
- Constitution Party ( 2 )
- Constitutional Rights ( 1 )
- Construction Update ( 4 )
- Consumer Alert ( 4 )
- Contractors ( 1 )
- Cooking ( 1 )
- Corona Virus ( 24 )
- Coronation ( 1 )
- Correction ( 3 )
- Corruption ( 99 )
- Cosmos ( 2 )
- Counter Jihad ( 93 )
- Counter Terrorism ( 21 )
- County Commissioner ( 1 )
- County Manager ( 5 )
- Courts ( 17 )
- COVID-19 ( 286 )
- COVID-19 County Alert System ( 2 )
- COVID-19 Hospitalizations ( 3 )
- COVID-19 Vaccine ( 58 )
- COVID19 ( 1 )
- cowee ( 1 )
- Cowee Fire Department ( 2 )
- Cowee Mountain ( 2 )
- cowee school ( 5 )
- Cowee School of Arts and Heritage ( 1 )
- Cowee VFD ( 5 )
- crime ( 131 )
- crime\ ( 1 )
- Crimes Against Humanity ( 4 )
- critters ( 28 )
- crowd funding ( 2 )
- Crowd Sourcing ( 1 )
- Cuba ( 4 )
- Cullasaja ( 5 )
- Cullasaja Community Association ( 1 )
- Cullasaja Falls ( 1 )
- Cullasaja Gorge ( 5 )
- Cullasaja River ( 2 )
- Cullasaja VFD ( 4 )
- Cullowhee ( 23 )
- Cultural Heritage ( 1 )
- Cultural Marxism ( 11 )
- Current Events ( 1 )
- curriculum ( 1 )
- CVF ( 40 )
- Daily Briefing ( 14 )
- daily kos ( 15 )
- Daily Weather Briefing ( 3197 )
- Dale Folwell ( 2 )
- Dan Buettner ( 1 )
- Dan Eichenbaum ( 20 )
- Dani Burrows ( 1 )
- Daniel Coates ( 1 )
- Danny Reitmeier ( 2 )
- Data Manipulation ( 1 )
- Dave Linn ( 1 )
- David Adams ( 2 )
- David Key ( 1 )
- David Linn ( 1 )
- David Lynch ( 1 )
- Daylight Saving Time ( 4 )
- Debate ( 86 )
- debris flow ( 1 )
- Debt ( 3 )
- December 2017 Weather ( 3 )
- December 2018 County Commissioners ( 4 )
- December 2018 Events ( 1 )
- December 2018 Local Government ( 3 )
- December 2018 Public Safety ( 10 )
- December 2018 Weather ( 35 )
- December 2019 Local Government Meeting ( 3 )
- December 2019 Public Safety ( 2 )
- December 2019 Weather ( 31 )
- December 2020 COVID-19 ( 23 )
- December 2020 Local Government ( 3 )
- December 2020 Public Safety ( 1 )
- December 2020 Weather ( 30 )
- December 2021 COVID-19 ( 1 )
- December 2021 Local Government ( 3 )
- December 2021 Public Safety ( 1 )
- December 2021 Weather ( 32 )
- December 2022 ( 1 )
- Declaration of Independence ( 3 )
- DELTA 2020 ( 5 )
- Democrat ( 9 )
- Democrats ( 174 )
- demographics ( 6 )
- Denver 2008 DNC ( 15 )
- DEQ ( 4 )
- Derek Roland ( 10 )
- Development ( 2 )
- Developmental Language Disorder ( 1 )
- Dhimmitude ( 1 )
- dhs ( 3 )
- Dick Armey ( 1 )
- Dick Cheney ( 5 )
- Dicks Creek Fire ( 2 )
- digital art ( 12 )
- Dillsboro ( 8 )
- Dinah Mashburn ( 1 )
- Direct Action ( 4 )
- Dirty Tricks ( 16 )
- disaster ( 51 )
- Discovery 13 ( 1 )
- disease ( 8 )
- District Attorney Ashley Welch ( 9 )
- District Court Judge ( 2 )
- DNC ( 14 )
- Documentary ( 10 )
- Dodie Allen ( 3 )
- DOGWOOD HEALTH TRUST ( 2 )
- DOJ ( 1 )
- Domestic Violence ( 2 )
- Don Yelton ( 3 )
- Donald Rumsfeld ( 3 )
- Donald Trump ( 23 )
- Donna Forga ( 2 )
- Donora Smog ( 1 )
- DORIAN 2019 ( 10 )
- Doris Miller ( 1 )
- Dr Thomas McNish ( 1 )
- DRAKE SOFTWARE ( 3 )
- drill ( 6 )
- drone ( 3 )
- drought ( 7 )
- drug culture ( 12 )
- drugs ( 18 )
- Dry Falls ( 4 )
- DST ( 2 )
- Duke Energy ( 19 )
- Duke LifePoint ( 1 )
- Duncan Hunter ( 5 )
- DuoTech ( 1 )
- Duverger ( 2 )
- Dvorak ( 1 )
- Early Voting ( 2 )
- earthquake ( 22 )
- EAS ( 1 )
- Easter ( 7 )
- EBCI ( 5 )
- eBooks ( 2 )
- ECBI ( 10 )
- Economic Development ( 21 )
- Economic Fascism ( 1 )
- economic socialism ( 93 )
- Economy ( 104 )
- Ed Krause ( 9 )
- Ed Morrissey ( 9 )
- EDA ( 1 )
- EDC ( 3 )
- EdNC ( 1 )
- Education ( 83 )
- Egypt ( 2 )
- Elbie Powers ( 1 )
- Election 2013 ( 6 )
- Election 2014 ( 19 )
- Election 2015 ( 9 )
- Election 2016 ( 9 )
- Election 2017 ( 4 )
- Election Day 2018 Storms ( 1 )
- Elections ( 68 )
- Electoral College ( 2 )
- Electrical Vehicles ( 1 )
- Elena Kagan ( 1 )
- Eletion 2024 ( 1 )
- Elijah Cummings ( 1 )
- elk ( 1 )
- Emergency Shelters ( 1 )
- Eminent Domain ( 1 )
- emoticons ( 2 )
- Employee Service Awards ( 2 )
- Enablers of Jihad ( 41 )
- Enablers of the Left ( 9 )
- End of the Line ( 1 )
- Energy ( 14 )
- engineering ( 1 )
- Entegra Bank ( 1 )
- entertainment ( 189 )
- Enviromentalism ( 3 )
- Environmental Lunacy ( 46 )
- Eric Cantor ( 1 )
- Eric Giles ( 2 )
- Erika Franzi ( 1 )
- Erlanger ( 1 )
- ESA ( 1 )
- Essays ( 5 )
- ETA 2020 ( 2 )
- Ethan Wingfield ( 1 )
- Ethics ( 1 )
- Eurabia ( 17 )
- Europe ( 19 )
- EUSSR ( 2 )
- Event ( 57 )
- Executive Order ( 2 )
- experiment ( 3 )
- Exploration ( 46 )
- exposing hypocrisy ( 46 )
- Extra Session I 2017-2018 Biennium ( 1 )
- f ( 1 )
- FAA ( 2 )
- FaceBook ( 11 )
- Facebook Alternatives ( 3 )
- Facing Evil ( 17 )
- Fairness Doctrine ( 9 )
- Fake News Stories ( 3 )
- Falcon Heavy ( 3 )
- Falklands ( 1 )
- fcc ( 2 )
- February 2019 Local Government ( 5 )
- February 2019 Public Safety ( 2 )
- February 2019 Weather ( 30 )
- February 2020 Local Government ( 6 )
- February 2020 Public Safety ( 11 )
- February 2020 Weather ( 30 )
- February 2021 Local Government ( 6 )
- February 2021 Weather ( 28 )
- February 2021COVID-19 ( 16 )
- February 2022 Weather ( 29 )
- Federal Budget ( 1 )
- Federal Oppression ( 28 )
- FEMA ( 5 )
- Ferebee Fire ( 1 )
- Ferebee Memorial Picnic Area ( 1 )
- Fern Shubert ( 5 )
- Festival ( 54 )
- FHS Panthers ( 3 )
- Field Trip ( 1 )
- Film ( 1 )
- fine art ( 26 )
- fire ( 20 )
- Fire Danger ( 2 )
- Fire Marshal ( 2 )
- fireball ( 1 )
- Firefighter Memorial Day 2020 ( 1 )
- Firefighter Memorial Day 2021 ( 1 )
- Fireworks ( 3 )
- First Citizens Bank ( 1 )
- First United Methodist Church ( 2 )
- fishing ( 1 )
- Flag Alert ( 127 )
- Flags ( 10 )
- Flashback ( 1 )
- Flashlight Vigil ( 3 )
- Flood Advisory ( 9 )
- Flood Plain Ordinance ( 5 )
- Flood Warning ( 7 )
- Flood Watch ( 19 )
- Flooding ( 6 )
- Floor Proceedings ( 2 )
- FLORENCE 2018 ( 11 )
- Flowers ( 20 )
- fog ( 8 )
- Folk Heritage Association of Macon County ( 1 )
- Fontana Regional Library ( 9 )
- Food Insecurity ( 2 )
- Food Supply ( 7 )
- FOP81 ( 5 )
- For Sale ( 1 )
- forg ( 1 )
- Forum ( 51 )
- Fostering ( 1 )
- Founding Documents ( 1 )
- Founding Fathers ( 1 )
- Fox News ( 7 )
- fracking ( 1 )
- france ( 4 )
- Frank Wood ( 3 )
- Franklin ( 228 )
- Franklin 2016 budget ( 6 )
- Franklin 2017 Budget ( 3 )
- Franklin 2018 Budget ( 1 )
- Franklin Aldermen ( 168 )
- Franklin ATC Committee ( 1 )
- Franklin ATC Committee. tourism ( 1 )
- Franklin Chamber of Commerce ( 4 )
- Franklin Church of God ( 1 )
- Franklin Comprehensive Plan ( 4 )
- Franklin Fire Department ( 15 )
- Franklin Folk Festival ( 11 )
- Franklin Ford Fire ( 1 )
- Franklin Forward ( 1 )
- Franklin Garden Club ( 3 )
- Franklin High School ( 4 )
- Franklin High School Grant ( 1 )
- franklin nc ( 54 )
- Franklin Planning Boad ( 1 )
- Franklin Planning Board ( 7 )
- Franklin Police ( 9 )
- Franklin Public Works ( 1 )
- Franklin TDA ( 27 )
- Franklin TDA 2016 ( 2 )
- Franklin TDA 2018 ( 2 )
- Franklin TDA 2020 ( 1 )
- Franklin Town Council ( 58 )
- Franklin Town Council 2021 Meetings ( 1 )
- Franklin Town Council February 2019 Meeting ( 9 )
- Franklin Town Manager ( 1 )
- Franklin VFD ( 6 )
- Franklin Young Progressionals ( 2 )
- FranklinGov ( 3 )
- FranklinNC ( 3 )
- Franz Lachner ( 1 )
- Franz Schubert ( 1 )
- FRED 2020 ( 1 )
- FRED 2021 ( 3 )
- Fred Smith ( 7 )
- Fred Thompson ( 18 )
- Free Markets ( 21 )
- Free Spech ( 2 )
- Free Speech ( 16 )
- freedom ( 26 )
- Freedom and Land Rights Coalition ( 1 )
- Freedom Folks ( 35 )
- Freedom Friday ( 1 )
- Freedom of the Press ( 2 )
- Freedom Works ( 19 )
- FReepers ( 2 )
- Freeze Warning ( 2 )
- FRiends Of the Greenway ( 1 )
- Friends of the Macon County Library ( 3 )
- FROGS ( 1 )
- Frontier Communications ( 2 )
- Frost Advisory ( 3 )
- frostbite ( 1 )
- FTX Collapse ( 1 )
- Full Circle Recovery Center ( 1 )
- fun ( 48 )
- Fund Raiser ( 22 )
- G+ Photo Walk ( 2 )
- Gambling ( 5 )
- Gardening ( 10 )
- Gardner Museum ( 2 )
- Gary Shields ( 1 )
- Gary Shileds ( 1 )
- Gas Crunch ( 12 )
- Gates of Vienna ( 12 )
- Gathering of Eagles ( 9 )
- Gay Pride ( 1 )
- Geert Wilders ( 1 )
- General Assembly ( 178 )
- General Election ( 27 )
- George Floyd ( 3 )
- George HW Bush ( 3 )
- George Irwin ( 1 )
- George W. Bush ( 40 )
- George Washington ( 4 )
- Ginseng ( 6 )
- Gitmo ( 2 )
- glenn beck ( 22 )
- Global Ice Age ( 46 )
- Global Tax ( 3 )
- global warming ( 48 )
- God ( 17 )
- Goebbels Would Be Proud ( 1 )
- GONZALO 2020 ( 2 )
- Google ( 1 )
- Google Maps ( 1 )
- Google+ ( 27 )
- GOP ( 303 )
- GORDON 2018 ( 2 )
- Gordon Smith ( 3 )
- Gossip ( 5 )
- GOTV ( 1 )
- Governor ( 9 )
- Graffiti ( 1 )
- Graham County ( 3 )
- Grant Application ( 2 )
- grants ( 5 )
- grass roots ( 25 )
- Great Britain ( 5 )
- Great Smokies ( 3 )
- Greenway ( 7 )
- Greg Newman ( 9 )
- ground breaking ( 1 )
- Groundhog Day ( 4 )
- guest commentary ( 29 )
- Gun ( 1 )
- gun rights ( 34 )
- Gun Sanctuary ( 1 )
- Gustav ( 3 )
- hail ( 1 )
- Hail Mary ( 1 )
- halloween ( 2 )
- Hamas ( 19 )
- Hamfest ( 1 )
- Hanna ( 4 )
- HANNA 2020 ( 1 )
- Hans Pfitzner ( 1 )
- Harm Reduction ( 1 )
- Harris Regional Hospital ( 3 )
- Harry Reid ( 1 )
- Hasan Harnett ( 1 )
- Hate-Filled Lefties ( 25 )
- Hayden Rogers ( 7 )
- Haywood County ( 32 )
- Haywood EMC ( 2 )
- Hazard Mitigation Plan ( 1 )
- HAZEL 1954 ( 1 )
- HCA ( 11 )
- health ( 7 )
- Health Care ( 6 )
- Heat ( 4 )
- Heat Index ( 2 )
- Heath Shuler ( 136 )
- HELENE 2024 ( 33 )
- Helicopter Crash ( 1 )
- Hemp ( 1 )
- Henderson County ( 12 )
- Here ( 1 )
- Herman Cain ( 2 )
- hero ( 27 )
- heroes ( 32 )
- hidden ( 2 )
- High School Sports ( 5 )
- Highlands ( 23 )
- Highlands Commissioners ( 10 )
- Highlands School ( 1 )
- Highlands VFD ( 1 )
- Highlands-Cashiers Hospital ( 2 )
- Hillary Clinton ( 57 )
- Hillsdale ( 1 )
- history ( 162 )
- HK Edgerton ( 4 )
- hn McCain ( 1 )
- Hoaxes ( 3 )
- Hobbies ( 11 )
- Holiday ( 142 )
- Holly Springs Plaza ( 1 )
- Hollyweird ( 2 )
- holocaust ( 8 )
- Homeland Security ( 20 )
- Homelessness ( 5 )
- Homosexual Agenda ( 11 )
- Honor Vets ( 3 )
- Hospice ( 1 )
- HR 3200 ( 8 )
- Hugo Chavez ( 7 )
- hulu ( 3 )
- Human Resources ( 1 )
- Human Spacefilght ( 70 )
- Human Spaceflight ( 15 )
- Human Trafficking ( 1 )
- Humor ( 83 )
- Hunger Awareness Month ( 1 )
- hunting ( 1 )
- Hurricane HARVEY 2017 ( 10 )
- Hurricane HAZEL ( 1 )
- Hurricane IRMA ( 15 )
- HUrricane Local Statement ( 1 )
- Hurricane NATE ( 2 )
- Hurricane Rita ( 1 )
- Hurricane Tracking ( 31 )
- hysteria ( 4 )
- IAN 2022 ( 4 )
- iCaucus ( 1 )
- ICE Raid ( 1 )
- Ice Storm ( 2 )
- IDA 2021 ( 5 )
- IDALIA ( 1 )
- IDALIA 2023 ( 1 )
- Idiot Rand Paul Supporters ( 1 )
- Idiot Ron Paul Supporters ( 64 )
- idiots ( 57 )
- Ike ( 15 )
- illegal alien crime ( 19 )
- illegal aliens ( 73 )
- illegal immigration ( 39 )
- immigration ( 2 )
- Impeachment Hearings ( 3 )
- In Brief ( 1 )
- Inauguration ( 4 )
- Income Tax ( 2 )
- Independence Day ( 9 )
- Index of Local Meetings ( 2 )
- India ( 8 )
- Infectious Disease ( 1 )
- InfoGraphic ( 7 )
- Informe COVID-19 ( 1 )
- Infrastructure ( 2 )
- Ingles Markets ( 6 )
- insight on freedom ( 3 )
- Inspirational ( 2 )
- Insurance ( 3 )
- Insurrection ( 5 )
- Interesting ( 41 )
- Internet ( 31 )
- Internet Outage ( 2 )
- Intifada ( 1 )
- Investigation ( 5 )
- Iotla Bridge Gauge ( 2 )
- Iotla Valley Elementary ( 1 )
- IPAWS ( 1 )
- Iran ( 34 )
- Iraq ( 80 )
- IRS ( 2 )
- Isaac ( 1 )
- ISASIAS 2020 ( 3 )
- islam ( 49 )
- israel ( 130 )
- j ( 1 )
- Jack Horton ( 3 )
- jackson county ( 96 )
- Jackson County Commissioners ( 2 )
- Jackson County Schools ( 1 )
- James Burke ( 1 )
- James Howard ( 4 )
- James Madison ( 1 )
- james Spann ( 1 )
- Jan 2017 weather ( 3 )
- Jane Hipps ( 3 )
- January 2018 Weather ( 1 )
- January 2019 Eclipse ( 1 )
- January 2019 Local Government ( 3 )
- January 2019 Weather ( 32 )
- January 2020 Executive Summaries ( 1 )
- January 2020 Local Government ( 2 )
- January 2020 Public Safety ( 32 )
- January 2020 Weather ( 28 )
- January 2021 COVID19 ( 7 )
- January 2021 Local Government ( 2 )
- January 2021 National News ( 6 )
- January 2021 Ntional News ( 1 )
- January 2021 Weather ( 30 )
- January 2022 ( 3 )
- January 2022 COVID-19 ( 1 )
- January 2022 Local Government ( 2 )
- January 2022 Public Safety ( 1 )
- January 2022 Weather ( 30 )
- January 6th Committee ( 1 )
- Japan ( 3 )
- Jason Arnold ( 1 )
- JAXA ( 1 )
- Jay Gibson ( 1 )
- Jay Rockefeller ( 1 )
- jazz ( 2 )
- JD Hayworth ( 2 )
- Jeff Bezos ( 1 )
- Jeff Flake ( 1 )
- Jeff Hunt ( 4 )
- Jeff Miller ( 26 )
- Jewish ( 1 )
- jihad ( 135 )
- JIhad Watch ( 2 )
- Jim Davis ( 30 )
- Jim DeMint ( 1 )
- Jim Long ( 1 )
- Jim Moore ( 1 )
- JimBo Ledford ( 1 )
- Jimmy Carter ( 1 )
- Jimmy Goodman ( 2 )
- Jimmy Tate ( 4 )
- Joe Biden ( 31 )
- Joe Collins ( 1 )
- Joe Sam Queen ( 2 )
- Joe the Plumber ( 2 )
- john armor ( 42 )
- John Batchelor ( 76 )
- John Boehner ( 5 )
- John DeVille ( 4 )
- John Edwards ( 10 )
- John Kerry ( 2 )
- John Lewis ( 1 )
- John Locke Foundation ( 4 )
- John McCain ( 157 )
- John Paul Stephens ( 1 )
- John Shearl ( 2 )
- John Snow ( 10 )
- John Tedesco ( 1 )
- John Thune ( 1 )
- Joint Meeting ( 1 )
- Jokes ( 1 )
- Jon Huntsman ( 4 )
- Jones Gap Fire ( 1 )
- Josh Stein ( 5 )
- Josh Young ( 1 )
- Joyce Kilmer ( 1 )
- JPSS ( 1 )
- JS Bach ( 2 )
- July 2018 Local Government ( 1 )
- July 2018 State Government ( 1 )
- July 2018 Weather ( 4 )
- July 2019 Local Government Meetings ( 3 )
- July 2019 Weather ( 30 )
- July 2020 COVID-19 ( 29 )
- July 2020 Local Government Meetings ( 4 )
- July 2020 Weather ( 28 )
- July 2021 COVID-19 ( 1 )
- july 2021 Events ( 1 )
- July 2021 Local Government Meetings ( 7 )
- July 2021 Weather ( 30 )
- July 4 ( 2 )
- June 2016 Weather ( 1 )
- June 2018 Weather ( 3 )
- June 2019 Local Goivernment Meetings ( 3 )
- June 2019 Weather ( 32 )
- June 2020 COVID-19 ( 33 )
- June 2020 Local Government Meetings ( 4 )
- June 2020 Weather ( 29 )
- June 2021 COVID-19 ( 1 )
- June 2021 Local Government ( 1 )
- June 2021 Local News ( 1 )
- June 2021 Weather ( 30 )
- Juneteenth ( 1 )
- Jupiter ( 2 )
- Jupiter Broadcasting ( 2 )
- jury trail ( 1 )
- Justin Greene ( 1 )
- Justin Setser ( 2 )
- K9 ( 1 )
- K9 Zee ( 1 )
- Kamala Harris ( 4 )
- Karen Wallace ( 1 )
- Karl Gillespie ( 15 )
- Katie Dean ( 1 )
- Kay Hagan ( 8 )
- Keith Smith ( 2 )
- Ken Bagwell ( 1 )
- Kenny West ( 11 )
- Kentucky ( 1 )
- Kevin Corbin ( 14 )
- Kevin Hayes ( 1 )
- Kevin Klatt ( 1 )
- KFI ( 3 )
- King Charles III ( 1 )
- Kmart ( 1 )
- Knob Fire ( 2 )
- Korean War ( 2 )
- Kristina Earwood ( 2 )
- L:aw Enforcement ( 1 )
- Land Trust for the Little Tennessee ( 1 )
- Land Use Plan ( 2 )
- Landslide ( 9 )
- Larry Moses ( 1 )
- Latin America ( 17 )
- Launch Abort ( 1 )
- LAURA 2020 ( 1 )
- law enforcement ( 55 )
- Law Enforcement Memorial day ( 6 )
- Lawfare ( 3 )
- Lawsuit ( 1 )
- LBJ Job Corps ( 1 )
- League of Women Voters ( 17 )
- Lee Anthony Nievez ( 1 )
- Lee Resolution ( 1 )
- lefty blogs ( 7 )
- Lefty Sex Crimes ( 12 )
- Legacy Media ( 63 )
- legislation ( 3 )
- Legislative Calendar ( 126 )
- Legislative Calender ( 150 )
- Leo Phillips ( 1 )
- Leslee Kulba ( 1 )
- Letter to the Editor ( 13 )
- LGF ( 6 )
- liberal talk ( 1 )
- Liberaltarians ( 1 )
- Libertarians ( 2 )
- Liberty ( 4 )
- Libya ( 5 )
- Lies From The Left ( 104 )
- Life During a Pandemic ( 11 )
- light ( 2 )
- lightning ( 5 )
- Linda Herman ( 1 )
- linkfest ( 17 )
- Linux ( 6 )
- litter ( 3 )
- LItter Sweep ( 1 )
- Little Green Footballs ( 1 )
- Little Tennessee River ( 12 )
- LIttle Tennessee River Greenway ( 1 )
- Live Blog ( 10 )
- Live Event ( 140 )
- Live Launch ( 3 )
- Live Leak ( 2 )
- live stream ( 38 )
- Local Attractions ( 41 )
- Local Authors ( 2 )
- Local Blogs ( 7 )
- Local Business ( 1 )
- local government ( 201 )
- Local Government Meetings ( 1 )
- Local IRMA Coverage ( 10 )
- Local News ( 336 )
- local politics ( 1 )
- lockout ( 2 )
- LOLCAT ( 11 )
- LOLPPL ( 2 )
- Long Ridge Fire ( 1 )
- LP ( 3 )
- LTE ( 7 )
- LTLT ( 1 )
- LUCY ( 1 )
- Luddites ( 2 )
- Ludwig van Beethoven ( 1 )
- Lumbee ( 1 )
- Lunacy ( 1 )
- Lunar Eclipse ( 6 )
- Lynda Bennett ( 2 )
- m ( 1 )
- MaaconGov ( 1 )
- Macon Advisory Board ( 1 )
- Macon Bank ( 1 )
- Macon Budget 2016 ( 8 )
- Macon Budget 2017 ( 1 )
- Macon Budget 2018 ( 3 )
- Macon Budget 2019 ( 1 )
- Macon Calendar ( 8 )
- Macon Commissioner Meetings ( 176 )
- Macon County ( 237 )
- Macon County Airport ( 2 )
- Macon County Airport Authority ( 8 )
- Macon County Animal Services ( 1 )
- Macon County Board of Commissioners ( 53 )
- Macon County Board of Commissioners Meetings ( 7 )
- Macon County Board of Education ( 49 )
- Macon County Board of Health ( 4 )
- Macon County Commissioners ( 21 )
- Macon County Communications ( 1 )
- Macon County Detention Facility ( 2 )
- Macon County Emergency Management ( 18 )
- Macon County EMS ( 3 )
- macon county heritage center ( 4 )
- Macon County Landfill ( 1 )
- Macon County NC ( 1 )
- Macon County News ( 4 )
- Macon County Planning Board ( 35 )
- Macon County Policies ( 1 )
- Macon County Public Health ( 30 )
- Macon County Public Library ( 30 )
- Macon County Republican Party ( 1 )
- Macon County Schools ( 6 )
- Macon County Sheriff Office ( 9 )
- Macon County Solid Waste ( 1 )
- Macon County Superior Court ( 6 )
- Macon EDC ( 9 )
- Macon Education ( 10 )
- Macon Entertainment ( 1 )
- Macon GOP ( 13 )
- Macon Health ( 3 )
- Macon Live ( 1 )
- Macon Media ( 270 )
- Macon Media World ( 1 )
- Macon Middle School ( 4 )
- Macon New Beginnings ( 4 )
- Macon Program for Progress ( 1 )
- Macon Safety ( 62 )
- Macon Science ( 3 )
- Macon Space ( 3 )
- Macon Traffic ( 4 )
- Macon Transit ( 3 )
- MaconCrime ( 23 )
- MaconEd ( 5 )
- macong ( 1 )
- MaconGov ( 342 )
- MaconHealth ( 1 )
- MaconMedia ( 2 )
- maconwx ( 9 )
- Madison Cawthorn ( 3 )
- Madison County ( 4 )
- Maggie Lauterer ( 1 )
- Maggie Valley ( 3 )
- Mailbag ( 1 )
- Main Spring ( 1 )
- Main Street ( 2 )
- Main Street Program ( 5 )
- Makers ( 1 )
- Makin Bots ( 1 )
- Mapping ( 1 )
- Maps ( 3 )
- March 2016 Meetings ( 1 )
- March 2018 Advisory Board Meetings ( 1 )
- March 2019 Local Government Meetings ( 3 )
- March 2019 Public Safety ( 1 )
- March 2019 Weather ( 33 )
- March 2020 COVID-19 Updates ( 8 )
- March 2020 Local Government Meetings ( 7 )
- March 2020 Public Safety ( 1 )
- March 2020 Weather ( 32 )
- March 2021 Columns ( 1 )
- march 2021 COVID-19 ( 8 )
- March 2021 Local Government ( 1 )
- March 2021 National News ( 1 )
- March 2021 Public Safety ( 1 )
- March 2021 Weather ( 31 )
- March 2022 Local Government ( 3 )
- March 2022 National and World News ( 1 )
- March 2022 Weather ( 17 )
- MARCO 2020 ( 1 )
- Mark Levin ( 4 )
- Mark Martin ( 1 )
- Mark Meadows ( 22 )
- Mark Melrose ( 2 )
- Mark Robinson ( 1 )
- Mark Sanford ( 2 )
- Marriage Amendment ( 1 )
- Mars ( 6 )
- MaryAnn Black ( 1 )
- mass ( 1 )
- mass shooting ( 9 )
- Mat 2020 Weather ( 1 )
- matching grant ( 1 )
- Matt Mittan ( 1 )
- May 2018 Meeting Segments ( 1 )
- May 2018 Weather ( 1 )
- May 2019 Local Government ( 4 )
- May 2019 Public Safety ( 1 )
- May 2019 Weather ( 31 )
- May 2020 COVID-19 ( 31 )
- May 2020 Local Government ( 4 )
- May 2020 Weather ( 30 )
- May 2021 COVID-19 ( 3 )
- May 2021 Local Government ( 6 )
- May 2021 Public Safety ( 2 )
- May 2021 Weather ( 29 )
- McCain Truth Files ( 8 )
- McDowell County ( 1 )
- MCSO ( 16 )
- Medallion of Honor ( 2 )
- Media Transparency Project ( 1 )
- Medicaid ( 3 )
- Medicaid Transformation ( 1 )
- Meeting Agenda ( 101 )
- Melissa Evans ( 1 )
- memorial ( 159 )
- Memorial Day ( 11 )
- menatl health ( 1 )
- mental health ( 3 )
- Merchants ( 1 )
- Mercury ( 3 )
- Mergers ( 1 )
- Merritt Fouts ( 1 )
- Mesoscale ( 4 )
- meteor shower ( 1 )
- Mexico ( 6 )
- MICHAEL 2018 ( 1 )
- Michael Steele ( 4 )
- Michele Bachman ( 5 )
- Michell Hicks ( 1 )
- Michelle Malkin ( 5 )
- MIddle East ( 17 )
- Mike Clampitt ( 2 )
- Mike Easley ( 1 )
- Mike Huckabee ( 19 )
- Mike Lewis ( 1 )
- Military ( 133 )
- Military Assets ( 6 )
- Minimum Housing Code ( 1 )
- Minnesota ( 1 )
- missed opporftunity ( 1 )
- Mission Health ( 35 )
- Mitch Daniels ( 2 )
- Mitt Romney ( 87 )
- MNF-Iraq ( 6 )
- Mohican32 ( 1 )
- moment of silence ( 2 )
- money ( 7 )
- Monkey Pox ( 1 )
- Monthly Reports ( 1 )
- moon ( 20 )
- moonbats ( 10 )
- Moose ( 1 )
- Moral Monday ( 1 )
- moratorium ( 1 )
- morning ( 26 )
- Moses Creek Fire ( 1 )
- Mountain Credit Union ( 1 )
- Mountain Findings ( 7 )
- Mountain Projects ( 1 )
- Mountain Valley Fire Department ( 4 )
- Mountain View Intermediate ( 3 )
- Mountain Views ( 1 )
- Mountain Xpress ( 7 )
- mountains ( 14 )
- movie ( 10 )
- Mozart ( 4 )
- Mr X ( 1 )
- mumpower ( 1 )
- music ( 35 )
- Music Monday ( 25 )
- musings ( 9 )
- mystery ( 1 )
- n ( 1 )
- N135CP ( 1 )
- N558MT ( 1 )
- N6075Q ( 1 )
- N70252 ( 1 )
- N80056 ( 1 )
- NAACP ( 2 )
- Nancy Pelosi ( 11 )
- Nantahala Community ( 10 )
- Nantahala Community Library ( 1 )
- Nantahala Gorge ( 4 )
- Nantahala NF ( 33 )
- NASA ( 80 )
- Nat Henry ( 1 )
- Nathan Henry ( 4 )
- Nathanael Moore ( 1 )
- national ( 1 )
- National Cathedral ( 2 )
- National Day of Mourning ( 2 )
- National Forests ( 10 )
- National Forests in North Carolina ( 7 )
- National Guard ( 1 )
- National News ( 2 )
- National Park Service ( 2 )
- National Peace Officers Memorial Day National Armed Forces Day ( 1 )
- National Popular Vote ( 1 )
- National Security ( 2 )
- NATO ( 3 )
- Natural Gas Leak ( 1 )
- Natural Resources ( 1 )
- nature ( 48 )
- navel-gazing ( 39 )
- NBC ( 5 )
- NC Agriculture Extension Office ( 1 )
- NC Big Sweep ( 1 )
- NC Congressional Districts ( 1 )
- NC Cooperative Extension ( 5 )
- NC Department of Commerce ( 2 )
- NC Department of Environmental Quality ( 2 )
- NC Dept of Agriculture ( 6 )
- NC DHHS ( 1 )
- NC DPI ( 2 )
- NC Forest Service ( 11 )
- NC Governor ( 26 )
- NC House ( 32 )
- NC Listen ( 4 )
- NC Senate ( 61 )
- NC SPIN ( 1 )
- NC State Board of Elections ( 1 )
- NC Tier Designations ( 1 )
- NC Utilities Commission ( 2 )
- NC Victory ( 1 )
- NC-05 ( 3 )
- NC-10 ( 10 )
- NC-11 ( 199 )
- NC-120 ( 7 )
- NC-50 ( 3 )
- NCACC ( 4 )
- NCAE ( 6 )
- NCDC ( 1 )
- NCDMV ( 7 )
- NCDOT ( 74 )
- NCDP ( 12 )
- NCDPI ( 1 )
- NCFS ( 7 )
- NCGA ( 16 )
- NCGA Project ( 257 )
- NCGOP ( 32 )
- NCHSAA ( 1 )
- NCLP ( 2 )
- NCSBE ( 1 )
- NCSHP ( 10 )
- ncwx ( 6 )
- Needmore Gauge ( 2 )
- Neighborhood Watch ( 1 )
- neo-Stalinist Tacttics ( 6 )
- Neptunus Lex ( 1 )
- nesting ( 1 )
- Nevada ( 1 )
- Never Forget ( 2 )
- New Hampshire ( 1 )
- New High School ( 1 )
- New Media ( 87 )
- New Media Journal ( 3 )
- new town bridge ( 1 )
- New Years Eve Skate Party ( 1 )
- news ( 62 )
- News Aggregation ( 1 )
- Newt Gingrich ( 42 )
- NFL ( 1 )
- NICOLE 2022 ( 2 )
- nikwasi ( 12 )
- Nikwasi Initiative ( 11 )
- Nikwasi Mound ( 11 )
- no apologies radio ( 1 )
- NOAA ( 3 )
- Nobel Prize ( 4 )
- noise ordinance ( 4 )
- Non-Profit Funding Pool 2018 ( 2 )
- non-profits ( 3 )
- north ( 1 )
- north carolina ( 264 )
- North Carolina Geological Survey ( 1 )
- North Carolina History ( 1 )
- North Carolina Judicial Branch ( 2 )
- North Korea ( 1 )
- nostalgia ( 6 )
- NOTAM ( 1 )
- Noth Carolina State Board of Elections ( 1 )
- nove ( 1 )
- November 2018 Almanac ( 5 )
- November 2018 Local Government Meetings ( 4 )
- November 2018 Public Safety ( 2 )
- November 2018 Weather ( 28 )
- November 2019 Events ( 1 )
- November 2019 Local Government ( 1 )
- November 2019 Weather ( 28 )
- november 2020 COVID-19 ( 13 )
- November 2020 Local Government ( 3 )
- November 2020 Weather ( 30 )
- November 2021 COVID-19 Update ( 7 )
- November 2021 Local Government ( 2 )
- November 2021 Weather ( 28 )
- Novermber 2019 Local Government Meetings ( 2 )
- NPS ( 1 )
- NRCC ( 3 )
- NTIA ( 1 )
- Nuclear Power ( 2 )
- nuisance ( 1 )
- Nutroots ( 8 )
- NWS ( 29 )
- NYC ( 7 )
- Obama ( 9 )
- Obama Cabinet ( 3 )
- Obama Sez ( 1 )
- ObamaCare ( 5 )
- Obituary ( 1 )
- obl ( 1 )
- Occupy Wall Street ( 3 )
- Octobe 2020 COVID-19 ( 2 )
- October 2018 Almanac ( 24 )
- October 2018 Public Safety ( 1 )
- October 2018 Weather ( 32 )
- October 2019 Local Government Meetings ( 1 )
- October 2019 Weather ( 27 )
- October 2020 COVID-19 ( 5 )
- october 2020 Local Government ( 3 )
- October 2020 Weather ( 30 )
- October 2021 COVID-19 ( 9 )
- October 2021 Events ( 1 )
- October 2021 Local Government ( 1 )
- October 2021 Public Safety ( 1 )
- October 2021 Weather ( 31 )
- Officer Involved Shooting ( 9 )
- Old Glory Radio ( 13 )
- Old Photos ( 1 )
- Old Salem Church ( 1 )
- old town bridge ( 4 )
- Olga Lampkin ( 1 )
- Online Media ( 61 )
- Oops ( 1 )
- Open House ( 1 )
- Open Source ( 2 )
- Open Thread ( 10 )
- Operation Cast Lead ( 51 )
- Operation Christmas Child ( 1 )
- Opioid Task Force ( 1 )
- Opioids ( 3 )
- Opposing Traitors ( 5 )
- Ordinance ( 3 )
- Orville Cowart ( 1 )
- Otto NC ( 3 )
- Otto VFD ( 2 )
- outage ( 8 )
- overheard ( 1 )
- PAC ( 2 )
- Pagans ( 3 )
- painting ( 4 )
- Pakistan ( 12 )
- parade ( 28 )
- Parker Meadows Property ( 6 )
- Parker Solar Probe ( 1 )
- Parking ( 3 )
- Parking Ordinance ( 1 )
- Parks and Recreation ( 3 )
- Parliamentary Procedures ( 1 )
- parody ( 3 )
- PARTF ( 1 )
- Party Conventions ( 63 )
- Pat Caddell ( 1 )
- Pat McCrory ( 24 )
- Patreon ( 3 )
- Patreon 2017 ( 1 )
- Patrick McHenry ( 10 )
- Patrick Taylor ( 1 )
- Patriotism ( 1 )
- Patti Halyburton Abel ( 3 )
- Paul Higdon ( 2 )
- Paul Newby ( 1 )
- Paul Ryan ( 10 )
- Pauline Avenue ( 1 )
- Peak Oil Debunking ( 5 )
- pearl harbor ( 6 )
- Peregine Falcon ( 3 )
- Peter Mosco ( 1 )
- petition ( 2 )
- Phil Berger ( 5 )
- Phil Drake ( 1 )
- Phil Haire ( 2 )
- Phillip Price ( 1 )
- Phillips Street ( 1 )
- Philosophy ( 3 )
- Photo Walk ( 1 )
- photoblog ( 226 )
- photoblog Franklin Garden Club ( 1 )
- photos ( 24 )
- Physics ( 1 )
- Pi Day ( 1 )
- Pinky Reid ( 1 )
- Pisgah Legal Services ( 6 )
- Pisgah National Forest ( 1 )
- Plan Revision ( 5 )
- planning ( 5 )
- Podcast ( 9 )
- Poetic Justice ( 3 )
- police ( 5 )
- Police Brutality ( 3 )
- Policy ( 1 )
- Policy Statement ( 1 )
- Political Correctness ( 13 )
- Political Thinkers ( 12 )
- Politics ( 109 )
- poll ( 1 )
- polls ( 62 )
- Pollution ( 6 )
- Pop Culture ( 7 )
- Pope ( 1 )
- Populism ( 1 )
- Power Outage Report ( 9 )
- prayer ( 17 )
- Precipitation Maps ( 1 )
- predictions ( 5 )
- Preparedness ( 28 )
- Prescribed Burns ( 10 )
- President ( 92 )
- President's Day ( 1 )
- Presidential Alert ( 2 )
- Press ( 14 )
- press conference ( 6 )
- Press Release ( 274 )
- Primaries ( 111 )
- primary ( 27 )
- privacy ( 1 )
- Private Property Rights ( 10 )
- Private Protperty Rights ( 1 )
- Private Space Flight ( 7 )
- Proclamation ( 5 )
- Progress NC ( 1 )
- Progressitarians ( 9 )
- Progressives ( 214 )
- Project Wayah ( 3 )
- Property Rights ( 8 )
- prostitution ( 1 )
- Protest ( 5 )
- PSA ( 107 )
- PSFNC ( 1 )
- PTC 2 2019 ( 1 )
- PTSD ( 1 )
- public comment ( 6 )
- Public Disk Golf Course ( 1 )
- public health ( 11 )
- Public Hearing ( 20 )
- Public Information Statement ( 2 )
- Public Private Partnership ( 1 )
- Public Safety ( 174 )
- Public Safety Log ( 2 )
- Public Service ( 3 )
- Public Skatepark ( 5 )
- Publicaciones en español marzo 2021 ( 1 )
- Pumpkinfest ( 1 )
- Pundits ( 3 )
- puns ( 1 )
- pursuit ( 2 )
- quadcopter ( 1 )
- Quarry Falls ( 1 )
- Queen Elizabeth II ( 2 )
- Quinn and Rose ( 6 )
- Quip Mode ( 1 )
- Quiz ( 23 )
- rabbits ( 1 )
- rabies ( 3 )
- Rabun County ( 3 )
- racism ( 24 )
- radio ( 71 )
- Rain ( 9 )
- Rainfall Map ( 1 )
- Raleigh ( 11 )
- Rally ( 36 )
- Ralph Nader ( 2 )
- Rand Paul ( 3 )
- Rankin Square ( 3 )
- REACH of Macon County ( 4 )
- Real Estate ( 1 )
- Reception ( 1 )
- Recount ( 1 )
- recovery ( 1 )
- recreation ( 7 )
- recycling ( 1 )
- Red State ( 4 )
- Red4EdNC ( 1 )
- Redistricting ( 10 )
- Referendum ( 1 )
- reflections ( 1 )
- Region A ( 1 )
- regional ( 1 )
- Register of Deeds ( 1 )
- Religious Freedom ( 14 )
- Remembering 9/11 ( 99 )
- Republican Liberty Caucus ( 1 )
- Republican Party ( 78 )
- Republican Primary ( 1 )
- Republicanism ( 7 )
- Republished ( 1 )
- Request fopr Proposals ( 1 )
- Resistance to Socialism ( 15 )
- Resolutions ( 1 )
- Resource ( 3 )
- Resurgent Russia ( 33 )
- Retention Pay ( 1 )
- Retirement ( 2 )
- Retirement Plans ( 1 )
- Retreat ( 3 )
- Revaluation ( 1 )
- Revolutionary Defeatism ( 13 )
- RFP ( 2 )
- ribbon cutting ( 3 )
- Richard Branson ( 1 )
- Richard Lightner ( 1 )
- Richard Moore ( 3 )
- Richard Rivette ( 1 )
- Rick Perry ( 7 )
- Rick Santorum ( 25 )
- Ricky Snyder ( 1 )
- Right to Work ( 1 )
- rights ( 2 )
- RINO ( 16 )
- riot ( 5 )
- RIP ( 21 )
- Riverside Gauge ( 6 )
- RKBA ( 13 )
- RL Clark ( 1 )
- RNC ( 17 )
- RNC Convention ( 29 )
- Road Geek ( 9 )
- Road Reports ( 1 )
- Robbie Hollan ( 1 )
- Robbie Holland ( 14 )
- Robotic Space Exploration ( 4 )
- Robots ( 1 )
- Rock Mountain Fire ( 3 )
- Roger West ( 5 )
- roli ( 1 )
- Roller Mill Road ( 1 )
- Ron Haven ( 7 )
- Ron Moore ( 1 )
- Ron Paul ( 82 )
- Ron Woodard ( 3 )
- Ronald Reagan ( 16 )
- Ronnie Beale ( 8 )
- RosCosmos ( 1 )
- rotary ( 3 )
- Roundabouts ( 1 )
- Roy Beck ( 1 )
- Roy Cooper ( 36 )
- Royal Family ( 1 )
- rtainment ( 1 )
- Ruby Drop ( 5 )
- Rudy Giuliani ( 7 )
- Rule 5 ( 1 )
- Rumors of War ( 14 )
- Rumors or War ( 1 )
- Rural Scenes ( 3 )
- Rush Limbaugh ( 24 )
- Russell Kirk ( 3 )
- russia ( 2 )
- Russian Invasion ( 1 )
- Ruth Bader Ginsburg ( 2 )
- Sales Tax ( 1 )
- Sallie Taylor ( 1 )
- SALLY 2020 ( 1 )
- Sam Greenwood ( 1 )
- Samaritans purse ( 2 )
- Sarah Conway ( 1 )
- Sarah Huckabee Sanders ( 1 )
- Sarah Palin ( 82 )
- Satellite Observation ( 6 )
- Saturday Matinee ( 1 )
- Saturn ( 1 )
- Saul Alinsky ( 9 )
- Saul Anuzis ( 1 )
- Savannah VFD ( 1 )
- Save Our Children ( 1 )
- Scarlet ( 5 )
- SCC ( 5 )
- Schedule ( 2 )
- School of Government ( 1 )
- schools ( 5 )
- science ( 120 )
- Science and Technology ( 1 )
- Science Fiction ( 26 )
- Science Thursday ( 1 )
- ScienceSaturday ( 3 )
- Scott Donaldson ( 1 )
- Scott Knibbs ( 5 )
- Scott Stump ( 2 )
- SCOTUS ( 23 )
- Scrutiny Hooligans ( 18 )
- search ( 3 )
- Sears Holdings ( 1 )
- SEBA ( 1 )
- Second Amendment ( 2 )
- SECU Foundation ( 1 )
- Seen From The Road ( 17 )
- self promotion ( 14 )
- Senate Legislation ( 3 )
- Senator Arlen Specter ( 5 )
- Senator Liddy Dole ( 13 )
- Senator Olympia Snowe ( 4 )
- Senator Richard Burr ( 27 )
- Senator Rick Rubio ( 1 )
- Senator Susan Collins ( 3 )
- Senior Center ( 4 )
- Senior Games ( 1 )
- Sept 11th ( 5 )
- September 2018 Almanac ( 17 )
- September 2018 Public Safety ( 1 )
- September 2018 Weather ( 10 )
- September 2019 Local Government Meetings ( 4 )
- September 2019 Weather ( 32 )
- September 2020 COVID ( 13 )
- September 2020 Local Government ( 2 )
- September 2020 Weather ( 22 )
- September 2021 COVID19 ( 19 )
- September 2021 Weather ( 31 )
- September 2021Local Government Meetings ( 2 )
- Serendipity ( 2 )
- Series ( 44 )
- Severe Outbreak 20170405 ( 3 )
- Severe Weather ( 20 )
- Sharia Law Watch ( 17 )
- Shaw Industries ( 1 )
- shelf cloud ( 1 )
- Shelly Foreman ( 1 )
- Shop Local ( 1 )
- sick\ ( 1 )
- SIGINT ( 2 )
- Siler Road ( 1 )
- silhouette ( 12 )
- silliness ( 66 )
- silly ( 1 )
- Sissy Pattillo ( 2 )
- Sk828 ( 3 )
- sky ( 6 )
- slide ( 3 )
- slide show ( 5 )
- Smoky Mountain Center for the Performing Arts ( 1 )
- Smoky Mountain Harm Reduction ( 1 )
- Smoky Mountain High School ( 1 )
- Smoky Mountain News ( 1 )
- Snow ( 45 )
- social district ( 2 )
- social media ( 6 )
- Social Networking ( 42 )
- Soil and Erosion Control ( 1 )
- Solar Cycle 24 ( 5 )
- Solar Cycles ( 6 )
- Solar Eclipse ( 15 )
- Soros Files ( 2 )
- Sound Off Buncombe ( 38 )
- South America ( 1 )
- South Carolina ( 6 )
- South Macon Elementary ( 2 )
- Southwestern Commission ( 2 )
- Soyuz ( 1 )
- space ( 47 )
- Space Accident ( 1 )
- Space Needs Analysis ( 1 )
- Space Station ( 21 )
- Space Tourism ( 1 )
- SpaceX ( 21 )
- spam ( 1 )
- SPC ( 1 )
- Speaker's Corner ( 1 )
- Special Meeting ( 4 )
- Special Session ( 1 )
- Spence Campbell ( 24 )
- sports ( 5 )
- stalinist tactics of the left ( 63 )
- Standard Time ( 1 )
- Starlink ( 3 )
- stars ( 1 )
- Starship ( 4 )
- STATE ( 3 )
- State Budget ( 3 )
- State Government ( 130 )
- State House ( 1 )
- State News ( 1 )
- State of Emergency ( 13 )
- State of the State ( 2 )
- State of the Union ( 4 )
- STEM ( 2 )
- Steve Woodsmall ( 1 )
- STIP ( 1 )
- Stock Market ( 1 )
- Stop The Harm ( 2 )
- storm chase ( 20 )
- Street Closing ( 4 )
- Streets of Franklin ( 1 )
- structure fire ( 8 )
- Student resource Officer ( 1 )
- stupid people ( 4 )
- Subdivision Ordinance ( 2 )
- Sugarfork ( 1 )
- Summer Activities ( 1 )
- Summer Solstice ( 1 )
- Summer Weather ( 1 )
- Summer Woodard ( 5 )
- sun ( 2 )
- Sunday Matinee ( 3 )
- sunrise ( 22 )
- sunset ( 16 )
- Sunshine ( 9 )
- Support The Troops ( 8 )
- Supreme Court ( 2 )
- Surrender Caucus ( 2 )
- Survival Tips ( 16 )
- Susan Fisher ( 1 )
- Susan Harris ( 2 )
- Susan Pons ( 2 )
- Suspicious Package ( 1 )
- Swain County ( 7 )
- Swine Flu 2009 ( 9 )
- sylva ( 40 )
- Syria ( 5 )
- t-shirt ( 1 )
- Tamara Zwinak ( 1 )
- taqqiya ( 1 )
- Tartan Hall ( 1 )
- taser ( 2 )
- Taste of Scotland ( 19 )
- Taxes ( 29 )
- TCOT ( 3 )
- Tea Party ( 54 )
- Technical Analysis ( 6 )
- Technology ( 87 )
- Tellico Fire ( 4 )
- Terrorism ( 183 )
- Terry Bellamy ( 1 )
- Terry Bradley ( 1 )
- test ( 5 )
- Texas ( 4 )
- TFR ( 1 )
- TGS ( 1 )
- Thanksgiving ( 10 )
- The Action Club ( 5 )
- The American Rescue Plan ( 1 )
- The Cone of Uncertainty ( 1 )
- The Franklin Press ( 1 )
- The Gathering Storm ( 3 )
- The Great Game ( 1 )
- the left ( 5 )
- The McLaughlin Group ( 3 )
- The Names ( 2 )
- The Southern Scoop ( 2 )
- theories ( 1 )
- This Week ( 1 )
- Thom Tillis ( 1 )
- Thomas McNish ( 1 )
- Thunder Tech ( 15 )
- Thundercast ( 6 )
- thunderstorm ( 10 )
- Thundertorial ( 2 )
- Tiangong-1 ( 1 )
- Tier Rankings ( 1 )
- Tim Moffitt ( 2 )
- Tim Pawlenty ( 6 )
- Tim Peck ( 2 )
- time lapse ( 11 )
- time laspe ( 30 )
- Timothy Johnson ( 5 )
- TJ Wright ( 1 )
- TNT ( 1 )
- Todd Raby ( 1 )
- Tom Apodaca ( 1 )
- Tom Delay ( 1 )
- Tom Tancredo ( 3 )
- Tommy Baldwin ( 1 )
- Tornado ( 11 )
- Tornado Watch ( 1 )
- tourism ( 32 )
- Town Gazebo ( 1 )
- Town Halls ( 14 )
- Town Liaisons ( 1 )
- Town Memorial Park ( 1 )
- Town of Franklin ( 28 )
- Town Personnel Policies ( 1 )
- town Summer Woodard ( 1 )
- transit ( 1 )
- Transparency ( 3 )
- Transportation ( 2 )
- transylvania county ( 4 )
- Trappalachia ( 1 )
- treason ( 11 )
- Trees ( 20 )
- Tribute ( 182 )
- Trooper Down ( 1 )
- Trooper Shawn Blanton ( 7 )
- Tropical ( 43 )
- Tropical Storm Warning ( 2 )
- Tropical Storm Watch ( 1 )
- TropWx ( 3 )
- Tsunami ( 1 )
- tubercolosis ( 1 )
- Twit-TV ( 3 )
- Twitter ( 70 )
- Typhoon H ( 1 )
- Typhoon Tip ( 1 )
- uav ( 2 )
- UDO ( 1 )
- UF ( 1 )
- UK ( 9 )
- Ukraine ( 1 )
- ULA ( 1 )
- UNC-TV ( 1 )
- uncategorized ( 4 )
- undisclosed location ( 2 )
- Unelected Government Bodies ( 1 )
- Unified Development Ordinance ( 1 )
- Unions ( 9 )
- United Nations ( 12 )
- United States Space Force ( 2 )
- Universal Health Care ( 42 )
- Urban Blight ( 1 )
- URTV ( 27 )
- US Capitol ( 5 )
- US Chamber of Commerce ( 1 )
- US Coast Guard ( 1 )
- US Congress ( 4 )
- US Constitution ( 55 )
- US Department of Defence ( 1 )
- US Department of Defense ( 1 )
- US House ( 25 )
- US Motto ( 1 )
- US Motto Action Committee ( 1 )
- US Navy ( 10 )
- US Navy SEALs ( 1 )
- US Senate ( 56 )
- US-23/74 ( 1 )
- US-441 ( 4 )
- US-64 ( 1 )
- USA ( 4 )
- USAF ( 1 )
- USCG ( 1 )
- USDA ( 5 )
- usfs ( 52 )
- usmc ( 8 )
- USS Oklahoma ( 1 )
- v ( 1 )
- Vaccine ( 4 )
- Vance Patterson ( 6 )
- Vandalism ( 1 )
- Vaya Health ( 3 )
- VDH ( 1 )
- Veepstakes ( 10 )
- Vegans ( 1 )
- Venezuela ( 7 )
- Venting ( 1 )
- Venture Local Franklin ( 10 )
- Veterans ( 50 )
- Veterans Day ( 7 )
- Vic Drummond ( 3 )
- Victory ( 16 )
- video ( 228 )
- Video Shows ( 1 )
- Vietnam Veterans Association Chapter 994 ( 2 )
- Vietnam Veterans Day ( 4 )
- Virgin Galactic ( 1 )
- Virginia ( 3 )
- Virginia Foxx ( 4 )
- virginia tech shooting ( 2 )
- virginia tech shootings ( 3 )
- Virus ( 1 )
- vlogcast ( 19 )
- Voice of the Resistance ( 3 )
- volcano ( 2 )
- Volunteers ( 5 )
- Voter registration ( 1 )
- Votes ( 23 )
- Voting Statistics ( 2 )
- WABC ( 4 )
- Walter Jones ( 2 )
- Walter Mondale ( 1 )
- War ( 74 )
- War Crimes ( 7 )
- Warren Cabe ( 4 )
- Washington DC ( 1 )
- water ( 14 )
- Water and Sewer ( 6 )
- Wayah bald ( 1 )
- Waynesville ( 1 )
- Waze ( 1 )
- wcu ( 67 )
- weather ( 215 )
- Weather Data ( 1 )
- Weather Prediction Center ( 1 )
- weather satellite ( 1 )
- weatherazzi ( 1 )
- Web 2.0 ( 1 )
- Wednesday Hero ( 2 )
- Weekend Happenings ( 2 )
- Weekend Weather ( 2 )
- Weird ( 21 )
- Weird Voting Systems ( 1 )
- West Carolina Report ( 46 )
- West Macon VFD ( 2 )
- West of the Balsams ( 10 )
- western civilization ( 45 )
- Western World politics ( 1 )
- WFB ( 1 )
- WHITE HOUSE ( 2 )
- Whitmire Property ( 8 )
- WHT ( 2 )
- WIC ( 1 )
- Widgets ( 1 )
- Wikipedia ( 2 )
- Wildfires ( 29 )
- wildlife ( 2 )
- William Gheen ( 2 )
- William Shatner ( 1 )
- Wind Advisory ( 14 )
- Winding Stairs Gap ( 1 )
- Window Wonderland ( 1 )
- Winter ( 31 )
- Winter Storm ( 10 )
- Winter Storm Watch ( 7 )
- Winter Wonderland ( 1 )
- Wisconsin ( 3 )
- WLOS-TV ( 2 )
- WMAL ( 2 )
- WMD ( 6 )
- WNC ( 54 )
- WNC Citizen Blog ( 31 )
- WNC Conservatives ( 9 )
- WNC Crime ( 1 )
- wnc news ( 4 )
- WNC Road Warriors ( 1 )
- WNCC-FM/WFSC-AM ( 1 )
- WNCCB2 ( 2 )
- Women's History Trail ( 2 )
- World News ( 2 )
- World War IV ( 313 )
- WW II ( 66 )
- WWIV ( 25 )
- WWNC ( 7 )
- wx 2016 0305 ( 1 )
- wx20230830 ( 1 )
- Y2K ( 1 )
- YAF ( 1 )
- Yom Hashoah ( 1 )
- You Don't Speak for Me ( 1 )
- Young Republicans ( 7 )
- youth ( 1 )
- Yuneec ( 1 )
- Z950 ( 4 )
- Zero Tolerance Insanity ( 2 )
- ZETA 2020 ( 7 )
- Zoning ( 9 )
Blog Archive
-
▼
2008
(
1582
)
-
▼
January
(
123
)
- U.S. Senator Dole Meets Secretly with Gates County...
- Republican Debate at Ronald Reagan Presidential Li...
- Republican Gubernatorial Candidate Justice Robert ...
- WCU Voter Registration by Ron Paul Supporters
- I Welcome My RINO Overlords
- Gathering of Eagles vs Veterans For Peace
- (VIDEO) 2008 State of the Union Address
- Some Final Polls, State of The Union
- Evangelicals for Mitt
- ALIPAC Open Letter to Paul & Romney Campaigns
- West Carolona Report for Jan 28th; Venus and Jupit...
- Remembering The Challenger 7
- Don’t treat the old and unhealthy, say UK Doctors
- Mother Replaces Son on Frontlines in Iraq
- Sunday Afternoon Blogburst
- Some Convenient Facts; Sun & Ocean Driving Climate...
- (VIDEO) Clinton on Iraqi WMD
- To ashevegas joe
- Politics, Democrat Style
- Retired Army Green Beret Court Martialed; Used We...
- The Champs Elysees Republicans
- Another One Bites The Dust...Kucinich Out
- The Definition of Rebate
- Bill, Hill, Alinsky, and Tearing Down Obama
- Largest Terrorist Forum Happily Proclaims: If Hill...
- Russian scientist says Earth could soon face new I...
- Pray For President Bush
- S-CHIP Veto Override Fails (Again!)
- "Asheville Municipal Golf Course " Flyover Tour
- Play Presidential Candidate Paintball!
- Britain Cracking Down On The Counterjihad?
- Who Needs Oil or Ethanol When You Can Grow Algae?
- My Man Fred Drops Out of the Race
- Asheville Progresives React To The Carolina Stompers
- (VIDEO) Democrats Debate In Myrtle Beach
- Task Force ODIN Kills 2,400 Bombers in Iraq!
- West Carolina Report and Ten Myths About Nuclear P...
- Patrick McHenry Conference Call
- Democratic Candidates Converge on Asheville, And S...
- Honor Major Andrew Olmsted: Give To The Children o...
- Anon Robo Callers Against Barack "Hussein" Obama
- Al-Qaeda in Iraq Update: Jan. 20
- The Problem With John McCain I
- Peak Oil: Meet Marcellus Black Shale
- As Another Snow Approaches, Dreams of Spring
- Spain Faces Terrorism Despite Fleeing Iraq
- Clinton Democrats Decry Union Thuggery In Nevada, ...
- A Special 2 Hour Gathering Storm Radio Show
- Snow Day Blogburst
- Winter Weather For WNC
- Democrat Debate Videos from Nevada
- 911 Audio Released From Tiger Attack
- Delegate Count After Michigan
- Press Release: Mumpower's Last Stand: Shuler Being...
- Mitt Romney Wins Michigan! Thank You Krazy Kos Kidz!
- You Can't Make This Stuff Up
- (VIDEO) Iraqi Freedom Minute 01-15-08
- West Carolina Report for Jan 15th Updated with video
- Senator Lamar Alexander Says: Stopping The Road T...
- Obama Concedes To Clinton Machine, Now Running For...
- Liberals Love John McCain
- Mr Amnesty Booed in Michigan
- New York Times Declares War on Veterans
- Sheepdog in Iraq
- Conflict With Taliban Heating Up
- Sunday Morning Blogburst
- Dirty Tricks by Liberals in Michigan GOP Primary
- Human Events Endorses Fred Thompson
- What do Iraqis think of the Americans?
- What Do Crack Dealers and Those Who Hire Illegal A...
- (VIDEO) Entire SC GOP Debate
- SC GOP Debate Coverage and Crazy Ron Paul
- Burr and Orr to Speak in Henderson County on March...
- Freedom Watch Afghanistan
- New Rasmussen Poll for South Carolina, National Nu...
- Introducing the USS New York (LPD-21)
- Keith Olbermann Caught Lying On Tape
- Did the Lancet Overestimate Iraqi Deaths?
- Another One Bites The Dust...Richardson Is Out
- Delegate Count After New Hampshire, and the Streng...
- How to Operate The New Widgets On My Sidebar
- Rasmussen National Tracking Poll for Jan 9th
- Hillary Not The Only Alinsky Acolyte In 2008
- New Hampshire Primary Results
- And Yet Another Presidential match-Maker Quiz
- Iraq Update for January 8th
- The Perfect Internet Storm
- Reuters/C-SPAN/Zogby poll for Jan 8th
- HIllary Clinton Has An Ace In The Hole
- West Carolina Report for January 8th
- Brownshirted Ron Paul Supporters Attack Radio Hos...
- Rush Limbaugh: Man of The Year
- Reuters/C-SPAN/Zogby GOP New Hampshire Primary
- Afghanistan National Security Forces Order of Battle
- (VIDEO) Prosperity or Poverty?
- Sunday Morning Blogburst
- R.I.P. Andrew Olmsted
- Pauleroids Misunderstand Iowa Caucus Results
- Iraqi Security Forces Order of Battle: January 200...
- Intrade Market Watch for Jan 4th
-
▼
January
(
123
)
-
Labels
- citizen journalism ( 807 )
- Barack Obama ( 394 )
- 2008 ( 393 )
- World War IV ( 313 )
- Concepts ( 304 )
- GOP ( 303 )
- north carolina ( 264 )
- NCGA Project ( 257 )
- Macon County ( 237 )
- Franklin ( 228 )
- video ( 228 )
- photoblog ( 226 )
- weather ( 215 )
- Progressives ( 214 )
- NC-11 ( 199 )
- entertainment ( 189 )
- Terrorism ( 183 )
- General Assembly ( 178 )
- Democrats ( 174 )
- Public Safety ( 174 )
- Conservatism ( 165 )
- breaking news ( 165 )
- Advisories Watches and Warnings ( 164 )
- history ( 162 )
- memorial ( 159 )
- John McCain ( 157 )
- Legislative Calender ( 150 )
- Holiday ( 142 )
- Live Event ( 140 )
- Heath Shuler ( 136 )
- jihad ( 135 )
- Military ( 133 )
- crime ( 131 )
- State Government ( 130 )
- science ( 120 )
- Primaries ( 111 )
- PSA ( 107 )
- 2012 ( 104 )
- Economy ( 104 )
- Lies From The Left ( 104 )
- Automated Post ( 102 )
- Remembering 9/11 ( 99 )
- jackson county ( 96 )
- Counter Jihad ( 93 )
- economic socialism ( 93 )
- Carl Mumpower ( 92 )
- President ( 92 )
- Buncombe County ( 91 )
- 2010 ( 90 )
- Blog Talk Radio ( 90 )
- Mitt Romney ( 87 )
- New Media ( 87 )
- Technology ( 87 )
- Debate ( 86 )
- Education ( 83 )
- Humor ( 83 )
- Sarah Palin ( 82 )
- Christian ( 81 )
- Iraq ( 80 )
- John Batchelor ( 76 )
- Christmas ( 75 )
- illegal aliens ( 73 )
- Activism ( 72 )
- radio ( 71 )
- Human Spacefilght ( 70 )
- wcu ( 67 )
- silliness ( 66 )
- 110th Congress ( 65 )
- Idiot Ron Paul Supporters ( 64 )
- Legacy Media ( 63 )
- Party Conventions ( 63 )
- astronomy ( 63 )
- stalinist tactics of the left ( 63 )
- polls ( 62 )
- Committees ( 61 )
- Online Media ( 61 )
- conservative activism ( 61 )
- conservative talk ( 61 )
- anti-American protesters ( 59 )
- Event ( 57 )
- Hillary Clinton ( 57 )
- commentary ( 57 )
- idiots ( 57 )
- law enforcement ( 55 )
- Festival ( 54 )
- Tea Party ( 54 )
- WNC ( 54 )
- blog burst ( 53 )
- clouds ( 51 )
- disaster ( 51 )
- Veterans ( 50 )
- islam ( 49 )
- fun ( 48 )
- global warming ( 48 )
- space ( 47 )
- Action Alert ( 46 )
- Environmental Lunacy ( 46 )
- Exploration ( 46 )
- Global Ice Age ( 46 )
- West Carolina Report ( 46 )
- exposing hypocrisy ( 46 )
- Appalachia ( 45 )
- Snow ( 45 )
- western civilization ( 45 )
- Announcements ( 44 )
- Communism ( 44 )
- Social Networking ( 42 )
- john armor ( 42 )
- Carolina Stompers ( 41 )
- Conservative Counter Protest ( 41 )
- Enablers of Jihad ( 41 )
- Local Attractions ( 41 )
- 111th Congress ( 40 )
- CVF ( 40 )
- George W. Bush ( 40 )
- sylva ( 40 )
- illegal immigration ( 39 )
- Sound Off Buncombe ( 38 )
- 910 ( 36 )
- Rally ( 36 )
- Freedom Folks ( 35 )
- Iran ( 34 )
- gun rights ( 34 )
- Resurgent Russia ( 33 )
- Conservative Thunder ( 32 )
- Haywood County ( 32 )
- NCGOP ( 32 )
- Hurricane Tracking ( 31 )
- WNC Citizen Blog ( 31 )
- alert ( 30 )
- time laspe ( 30 )
- Taxes ( 29 )
- guest commentary ( 29 )
- Federal Oppression ( 28 )
- critters ( 28 )
- General Election ( 27 )
- Senator Richard Burr ( 27 )
- hero ( 27 )
- Civil War ( 26 )
- Science Fiction ( 26 )
- freedom ( 26 )
- Hate-Filled Lefties ( 25 )
- grass roots ( 25 )
- Rush Limbaugh ( 24 )
- 5GW ( 23 )
- Audio ( 23 )
- Cullowhee ( 23 )
- SCOTUS ( 23 )
- Votes ( 23 )
- earthquake ( 22 )
- glenn beck ( 22 )
- Counter Terrorism ( 21 )
- Free Markets ( 21 )
- Space Station ( 21 )
- Autumn ( 20 )
- Conservative Revolution ( 20 )
- Homeland Security ( 20 )
- anti-Semitism ( 20 )
- storm chase ( 20 )
- Europe ( 19 )
- Freedom Works ( 19 )
- Hamas ( 19 )
- Mike Huckabee ( 19 )
- Taste of Scotland ( 19 )
- illegal alien crime ( 19 )
- Africa ( 18 )
- Beverly Perdue ( 18 )
- Fred Thompson ( 18 )
- Scrutiny Hooligans ( 18 )
- drugs ( 18 )
- Courts ( 17 )
- Eurabia ( 17 )
- Facing Evil ( 17 )
- God ( 17 )
- Latin America ( 17 )
- MIddle East ( 17 )
- Sharia Law Watch ( 17 )
- City Council ( 16 )
- Dirty Tricks ( 16 )
- Free Speech ( 16 )
- RINO ( 16 )
- Survival Tips ( 16 )
- Thunder Tech ( 15 )
- daily kos ( 15 )
- Climate ( 14 )
- DNC ( 14 )
- Energy ( 14 )
- al fin ( 14 )
- conspiracy theories ( 13 )
- Gates of Vienna ( 12 )
- Henderson County ( 12 )
- Lefty Sex Crimes ( 12 )
- drug culture ( 12 )
- China ( 11 )
- Cultural Marxism ( 11 )
- Franklin Folk Festival ( 11 )
- Hobbies ( 11 )
- Homosexual Agenda ( 11 )
- Nancy Pelosi ( 11 )
- Raleigh ( 11 )
- 911 Retards ( 10 )
- BCGOP ( 10 )
- Blogger Tips ( 10 )
- Documentary ( 10 )
- Gardening ( 10 )
- Patrick McHenry ( 10 )
- West of the Balsams ( 10 )
- Alternative Energy ( 9 )
- Asia ( 9 )
- Democrat ( 9 )
- Ed Krause ( 9 )
- Ed Morrissey ( 9 )
- Enablers of the Left ( 9 )
- Fairness Doctrine ( 9 )
- Gathering of Eagles ( 9 )
- Governor ( 9 )
- Progressitarians ( 9 )
- Saul Alinsky ( 9 )
- Swine Flu 2009 ( 9 )
- UK ( 9 )
- Zoning ( 9 )
- Dillsboro ( 8 )
- India ( 8 )
- Kay Hagan ( 8 )
- disease ( 8 )
- fog ( 8 )
- holocaust ( 8 )
- Charles Taylor ( 7 )
- Food Supply ( 7 )
- Hugo Chavez ( 7 )
- Republicanism ( 7 )
- Rudy Giuliani ( 7 )
- Swain County ( 7 )
- lefty blogs ( 7 )
- Chad Nesbitt ( 6 )
- Chinese Aggression Watch ( 6 )
- Quinn and Rose ( 6 )
- Thundercast ( 6 )
- demographics ( 6 )
- Any Way You Like It ( 5 )
- Babylon 5 ( 5 )
- Cherokee County ( 5 )
- Congress ( 5 )
- Dick Cheney ( 5 )
- Essays ( 5 )
- Great Britain ( 5 )
- Solar Cycle 24 ( 5 )
- Syria ( 5 )
- The Action Club ( 5 )
- Timothy Johnson ( 5 )
- slide show ( 5 )
- Cuba ( 4 )
- Direct Action ( 4 )
- HK Edgerton ( 4 )
- John Locke Foundation ( 4 )
- Madison County ( 4 )
- Texas ( 4 )
- constitution ( 4 )
- france ( 4 )
- hysteria ( 4 )
- Clay County ( 3 )
- Don Yelton ( 3 )
- Fake News Stories ( 3 )
- Global Tax ( 3 )
- Gordon Smith ( 3 )
- Graham County ( 3 )
- Hoaxes ( 3 )
- TCOT ( 3 )
- The Gathering Storm ( 3 )
- dhs ( 3 )
- Civitas Institute ( 2 )
- Class Warfare ( 2 )
- FReepers ( 2 )
- Gitmo ( 2 )
- Susan Pons ( 2 )
- Zero Tolerance Insanity ( 2 )
- Clean Coal ( 1 )
- Constellation Program ( 1 )
- Data Manipulation ( 1 )
- End of the Line ( 1 )
- George Irwin ( 1 )
- NC Congressional Districts ( 1 )
- Saul Anuzis ( 1 )
- Susan Fisher ( 1 )
- YAF ( 1 )
- taqqiya ( 1 )
Copyright © 2011
Thunder Pig
| Powered by
Blogger
























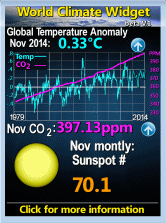


0 comments :
Post a Comment